D2
Администратор
- Регистрация
- 19 Фев 2025
- Сообщения
- 4,380
- Реакции
- 0
A massive ransomware campaign targeting QNAP devices worldwide is underway, and users are finding their files now stored in password-protected 7zip archives.
The ransomware is called Qlocker and began targeting QNAP devices on April 19th, 2021. Since then, there has been an enormous amount of activity in our support forum, and ID-Ransomware has seen a surge of submissions from victims.
According to reports from victims in a BleepingComputer Qlocker support topic, the attackers use 7-zip to move files on QNAP devices into password-protected archives. While the files are being locked, the QNAP Resource Monitor will display numerous '7z' processes which are the 7zip command-line executable.
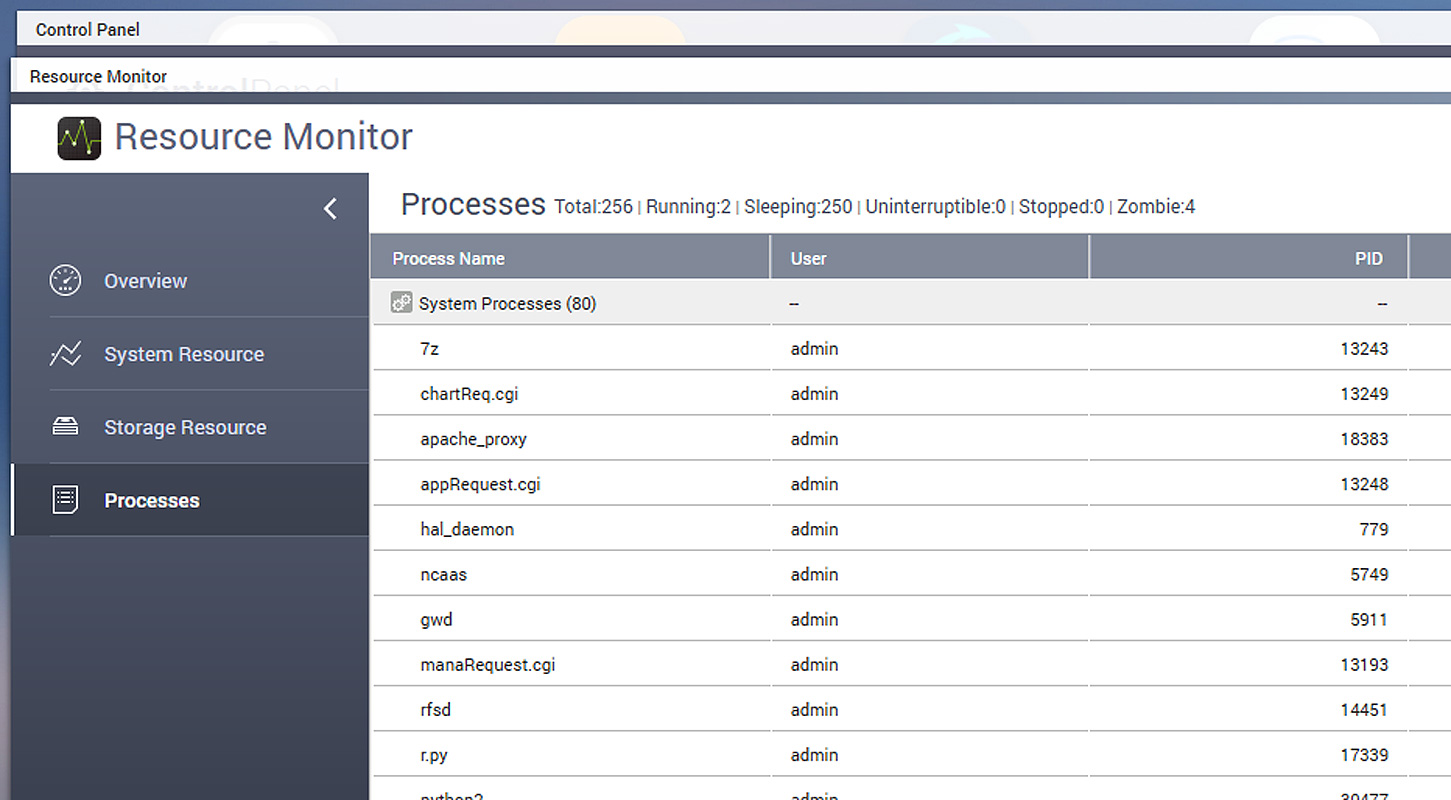
7zip seen running in the QNAP Resource Monitor
When the ransomware has finished, the QNAP device's files will be stored in password-protected 7-zip archives ending with the .7z extension. To extract these archives, victims will need to enter a password known only to the attacker.
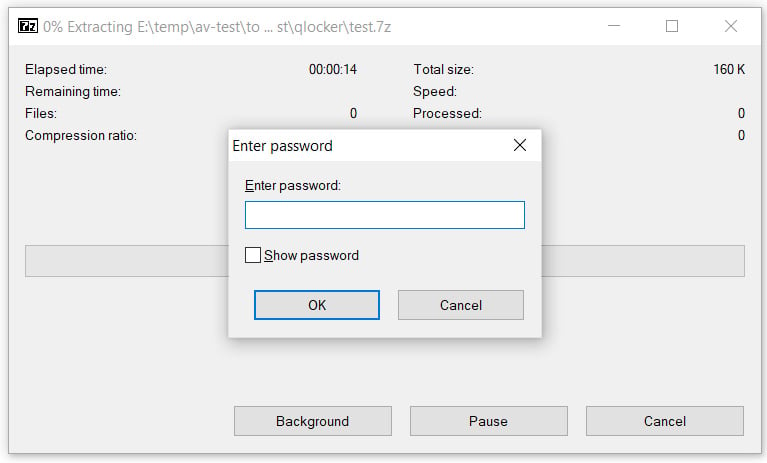
Password-protected 7zip archive
After QNAP devices are encrypted, users are left with a !!!READ_ME.txt ransom note that includes a unique client key that the victims need to enter to log into the ransomware's Tor payment site.
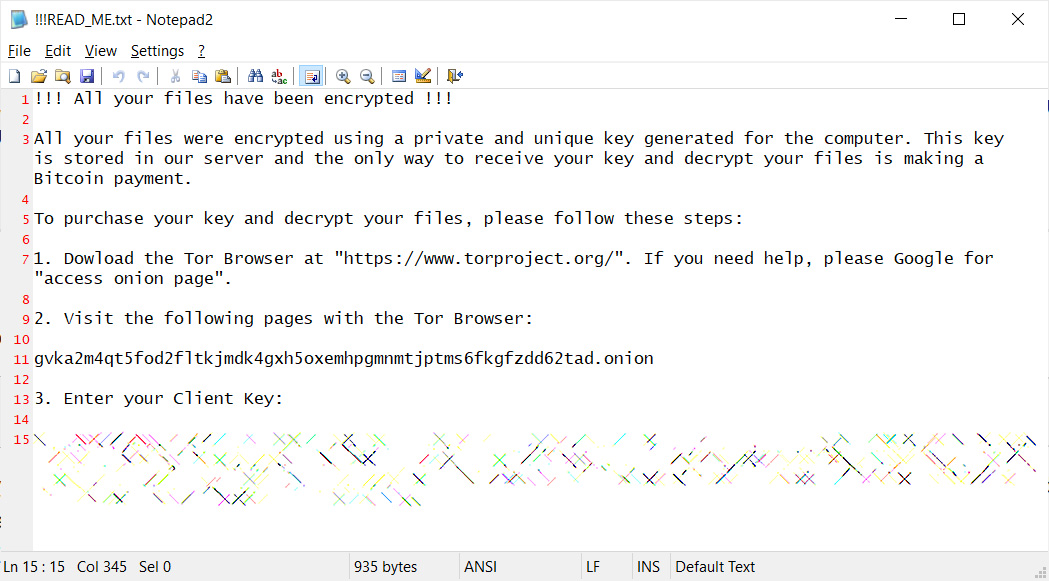
Qlocker ransom note
From the Qlocker ransom notes seen by BleepingComputer, all victims are told to pay 0.01 Bitcoins, which is approximately $557.74, to get a password for their archived files.
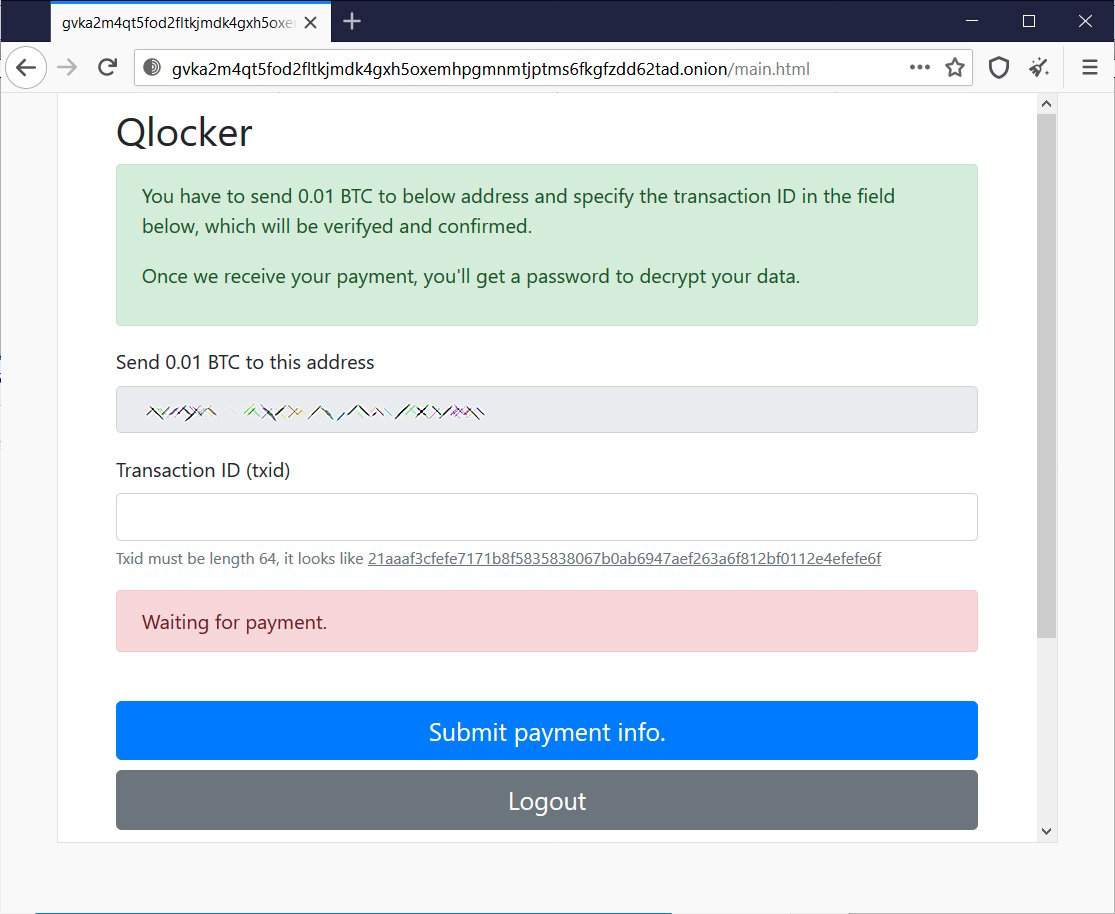
Qlocker Tor payment site
Update 4/22/21 12:44 AM EST: A weakness may have been found that could potentially allow victims to recover their files for free. We are still investigating this and will post an update around 10 AM EST, or possibly earlier..
Update 4/22/21 09:15 AM EST: Early this morning, BleepingComputer was contacted by Jack Cable about bug he discovered in the Qlocker Tor site that allowed users to recover their 7zip passwords for free.
Using this bug, victims could take a Bitcoin transaction ID from a person who had already paid the ransom and slightly alter it. When they submitted the altered transaction ID into the Qlocker Tor site, it accepted it as payment and displayed the victim's 7zip password.
Last night, Cable had been private helping people recover their passwords and arrangements were being made with Emsisoft to create a help system for victims to recover files.
Sadly, an hour after we learned of the bug, the ransomware operators caught on and fixed it.
QNAP fixed these two vulnerabilities on April 16th with the following descriptions:
QNAP told BleepingComputer that they believe Qlocker exploits the CVE-2020-36195 vulnerability to execute the ransomware on vulnerable devices.
Due to this, it is strongly recommended to update QTS, Multimedia Console, and the Media Streaming Add-on to the latest versions.
While this will not recover your files, it will protect you from future attacks using this vulnerability.
All your files were encrypted using a private and unique key generated for the computer. This key is stored in our server and the only way to receive your key and decrypt your files is making a Bitcoin payment.
To purchase your key and decrypt your files, please follow these steps:
1. Dowload the Tor Browser at "https://www.torproject.org/". If you need help, please Google for "access onion page".
2. Visit the following pages with the Tor Browser:
gvka2m4qt5fod2fltkjmdk4gxh5oxemhpgmnmtjptms6fkgfzdd62tad.onion
3. Enter your Client Key:
[client_key]
The ransomware is called Qlocker and began targeting QNAP devices on April 19th, 2021. Since then, there has been an enormous amount of activity in our support forum, and ID-Ransomware has seen a surge of submissions from victims.
According to reports from victims in a BleepingComputer Qlocker support topic, the attackers use 7-zip to move files on QNAP devices into password-protected archives. While the files are being locked, the QNAP Resource Monitor will display numerous '7z' processes which are the 7zip command-line executable.

7zip seen running in the QNAP Resource Monitor
When the ransomware has finished, the QNAP device's files will be stored in password-protected 7-zip archives ending with the .7z extension. To extract these archives, victims will need to enter a password known only to the attacker.

Password-protected 7zip archive
After QNAP devices are encrypted, users are left with a !!!READ_ME.txt ransom note that includes a unique client key that the victims need to enter to log into the ransomware's Tor payment site.

Qlocker ransom note
From the Qlocker ransom notes seen by BleepingComputer, all victims are told to pay 0.01 Bitcoins, which is approximately $557.74, to get a password for their archived files.

Qlocker Tor payment site
Update 4/22/21 12:44 AM EST: A weakness may have been found that could potentially allow victims to recover their files for free. We are still investigating this and will post an update around 10 AM EST, or possibly earlier..
Update 4/22/21 09:15 AM EST: Early this morning, BleepingComputer was contacted by Jack Cable about bug he discovered in the Qlocker Tor site that allowed users to recover their 7zip passwords for free.
Using this bug, victims could take a Bitcoin transaction ID from a person who had already paid the ransom and slightly alter it. When they submitted the altered transaction ID into the Qlocker Tor site, it accepted it as payment and displayed the victim's 7zip password.
Last night, Cable had been private helping people recover their passwords and arrangements were being made with Emsisoft to create a help system for victims to recover files.
Sadly, an hour after we learned of the bug, the ransomware operators caught on and fixed it.
At this point, there is no way to recover the files without a password, which can no longer be retrieved for free.Update: it looks like this may have been fixed by the ransomware operators, unfortunately. I apologize if I was not able to get to yours before it was fixed. In total decrypted around 50 keys worth $27k.Нажмите, чтобы раскрыть...
— Jack Cable (@jackhcable) April 22, 2021
QNAP believes they are using recent vulnerability
Recently QNAP resolved critical vulnerabilities that could allow a remote actor to gain full access to a device and execute ransomware.QNAP fixed these two vulnerabilities on April 16th with the following descriptions:
- CVE-2020-2509: Command Injection Vulnerability in QTS and QuTS hero
- CVE-2020-36195: SQL Injection Vulnerability in Multimedia Console and the Media Streaming Add-On
QNAP told BleepingComputer that they believe Qlocker exploits the CVE-2020-36195 vulnerability to execute the ransomware on vulnerable devices.
Due to this, it is strongly recommended to update QTS, Multimedia Console, and the Media Streaming Add-on to the latest versions.
While this will not recover your files, it will protect you from future attacks using this vulnerability.
Qlocker IOCs:
Associated Files:
!!!READ_ME.txtRansom note text:
!!! All your files have been encrypted !!!All your files were encrypted using a private and unique key generated for the computer. This key is stored in our server and the only way to receive your key and decrypt your files is making a Bitcoin payment.
To purchase your key and decrypt your files, please follow these steps:
1. Dowload the Tor Browser at "https://www.torproject.org/". If you need help, please Google for "access onion page".
2. Visit the following pages with the Tor Browser:
gvka2m4qt5fod2fltkjmdk4gxh5oxemhpgmnmtjptms6fkgfzdd62tad.onion
3. Enter your Client Key:
[client_key]