D2
Администратор
- Регистрация
- 19 Фев 2025
- Сообщения
- 4,380
- Реакции
- 0
Author: Shootem
Specifically for: xss.is
Table of Contents:
QKD is currently in various stages of implementation and testing in the following sectors:
Energy Sector:
Confirmed implementation at China State Grid
Pilot projects under EuroQCI
Security tests on SCADA systems in selected locations
Financial Sector:
Implementation in select banks in China (Bank of China, ICBC)
Pilot projects in other financial institutions
Security tests for high-value transactions
Military Infrastructure:
Research and development conducted by defense agencies
Demonstrations of the technology in satellite communications
Investments in quantum threat countermeasures
Telecommunications Sector:
Commercial deployments by China Telecom
Pilot projects with BT and Toshiba
Tests in backbone networks
So, let's begin!
QUANTUM KEY DISTRIBUTION (QKD):
Код: Скопировать в буфер обмена
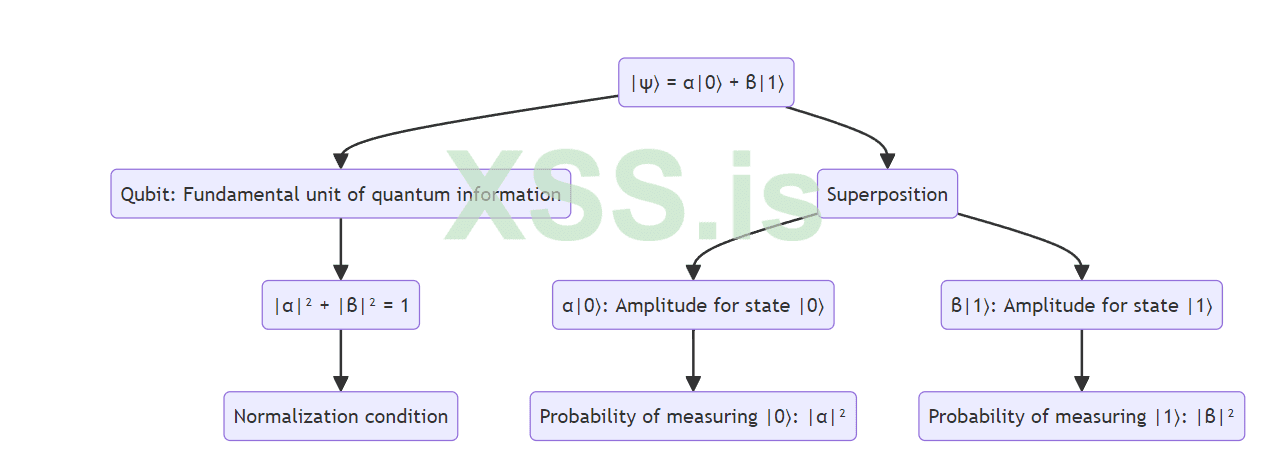
This quantum state represents the fundamental unit of quantum information (qubit).
To understand how this works, I must discuss the basic principles on which this distribution is based and why it is considered the highest known level of security in data transmission. Let's start with the most important concept—superposition: Imagine a coin. A normal coin has two sides: heads and tails. Before you toss it, you don’t know which side will be up, right? It could be heads or tails. You could also say it’s in an intermediate state, where it’s both heads and tails—until you check it. This is somewhat like superposition.
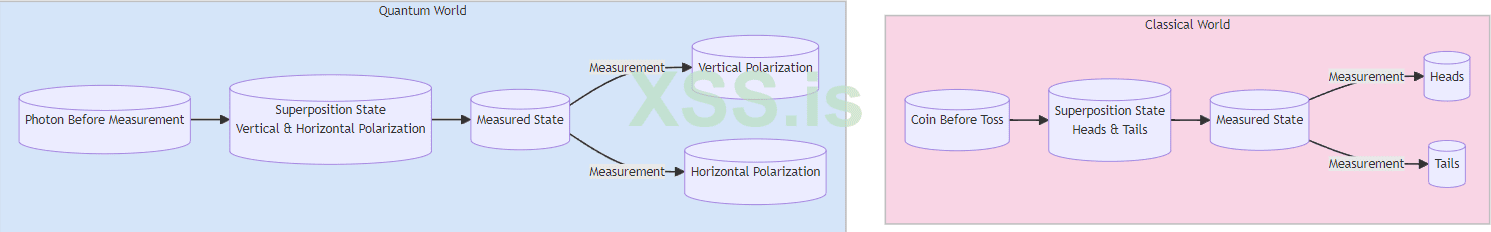
In the quantum world, instead of coins, we have particles, such as photons (particles of light). These particles can also be in multiple states "at once" until we measure them. For example, they can be in a superposition of polarization, vibrating both vertically and horizontally at the same time. Only when we "check" (measure) them do they "decide" on a specific state—vertical or horizontal.
QKD (Quantum Key Distribution) is a way to create a super-secret key to encrypt messages, thanks to superposition and another quantum trick called "entanglement". Entanglement: is like two magical coins that always land on the same side, no matter how far apart they are. Imagine you have one coin, and your friend has the other—on another continent! When you toss your coin and get heads, you instantly know that your friend’s coin is also heads, even though they haven’t tossed theirs yet. And the same goes if it were tails. It’s as if these coins are connected by an invisible thread and "talk" to each other instantly!
In the quantum world, entangled particles, like photons, behave similarly. If you measure the state of one entangled photon (for example, its polarization), you immediately know the state of the other entangled photon, even if it’s light-years away. You might think this sounds a bit "magical," but that’s how the quantum world works. And it’s this quantum entanglement, along with superposition, that makes QKD so secure. Any attempt to "eavesdrop" on these entangled photons by an outsider "breaks" them and changes their state, immediately revealing the presence of a spy. Speaking of measurement, let’s move on to Heisenberg’s Uncertainty Principle:
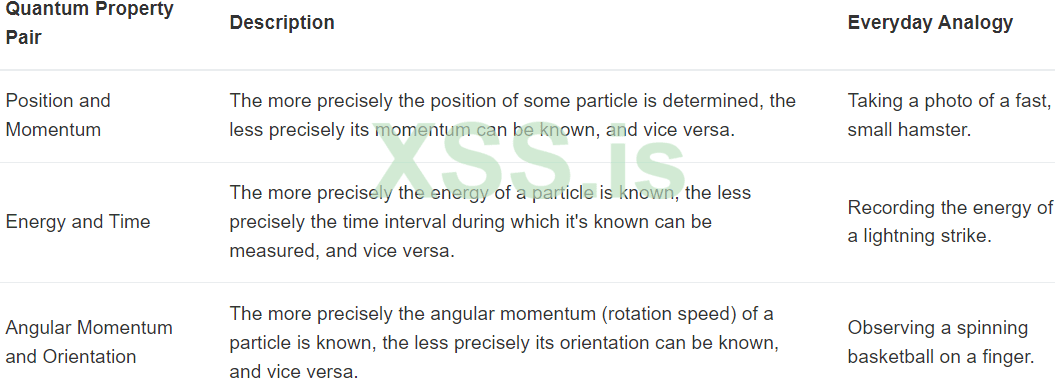
This principle, in short, tells us that in the quantum world, you can’t simultaneously know certain pairs of properties of particles, such as position and momentum (speed), with precision. The more accurately you know one, the less accurately you know the other. This isn’t due to imperfect instruments; it’s a fundamental property of the universe and a limitation of nature! Imagine it like this: you’re trying to take a photo of a small, fast hamster. You want to know where it is and how fast it’s running. The problem is, if you use a fast shutter speed to see exactly where it is, the hamster will be blurry, and you won’t know how fast it’s running. And if you use a long exposure to see how fast it’s running, the hamster will have moved, and you won’t know exactly where it was when you took the picture.
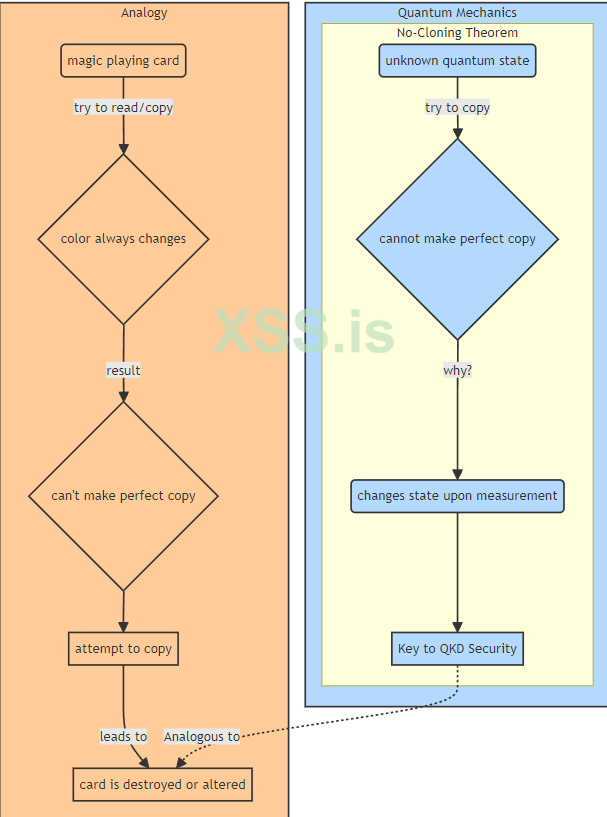
The last fundamental concept is the No-Cloning Theorem: Imagine you have a magic playing card that changes color every time you look at it—sometimes it’s red, sometimes blue, sometimes green. And you want to make a perfect copy of it. The problem is, every time you try to "read" it to copy it, its color changes! You’ll never be sure what color it originally was, so you’ll never make a perfect copy.
The no-cloning theorem in quantum mechanics states that you can’t make a perfect copy of an unknown quantum state, just like you can’t copy the color of this magic card. This is key to QKD security: if someone tries to "eavesdrop" on a quantum message (i.e., make a copy), they irreversibly change its original state, which the sender and receiver will immediately detect. It’s as if someone destroyed your magic card by trying to copy it.
As you now understand, thanks to superposition and entanglement, QKD allows the creation of a key that only the sender and receiver know is secure, and thanks to the No-Cloning Theorem, anyone who tries to intercept it will be instantly detected.
QBER (Quantum Bit Error Rate) is a key parameter determining the quality of quantum transmission:
Код: Скопировать в буфер обмена
The equation for determining the theoretical key generation rate (Key Rate) in the BB84 protocol is:
Код: Скопировать в буфер обмена
where:
DV-QKD:
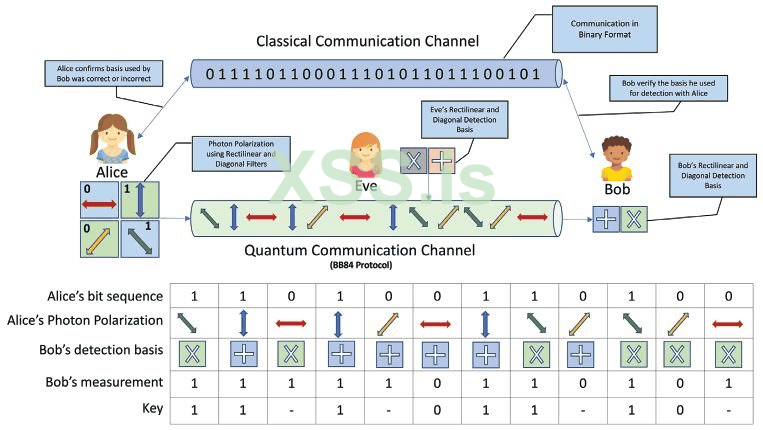
BB84 (Most common): The pioneering protocol, using the polarization of single photons. The sender (Alice) sends photons encoded in randomly chosen bases (e.g., vertical/horizontal or diagonal), and the receiver (Bob) randomly chooses measurement bases. After transmission, Alice and Bob publicly compare chosen bases, discarding results from incompatible bases. The remaining results form the raw key. Security is based on the uncertainty principle (mentioned earlier) and the No-Cloning Theorem—an eavesdropper (Eve) attempting to intercept and copy the photons will introduce detectable errors.
E91 (Ekert91):
Uses entangled pairs of photons. Alice and Bob each receive one photon from the entangled pair and perform measurements in different bases. Security arises from the violation of Bell's inequality in the event of eavesdropping. Eavesdropping is detected through statistical analysis of the correlations between Alice's and Bob's measurements.
SARG04:
A modification of BB84, it uses only one basis for encoding information and the other as "bait" for the eavesdropper. This increases efficiency compared to BB84 but is slightly less resistant to noise.
CV-QKD:
GG02 (Grosshans & Grangier 02):
Utilizes quadrature components of coherent light (lasers). The key is encoded in the amplitudes and phases of light pulses, measured by Bob. Security is based on the uncertainty principle for continuous variables. This protocol is relatively easy to implement using standard telecommunications technology.
There are also hybrid protocols and other variants, but the ones listed are the most significant and representative of different approaches to QKD.
Practical Implementation Details:
Existing QKD Networks:
Quantum Memory in QKD
Quantum memory is crucial for extending QKD networks:
of course QKD is not perfect on every level and like any new technology, it requires solving currently known problems, the most problematic of which are:
Range Limitations, current practical limitations:
Implementation Challenges:
Conclusions:
QKD has enormous potential in ensuring the security of information transmission. Although there are technological and economic challenges, intensive research and development are driving progress in terms of range, cost, and integration. QKD is a technology worth attention and further development. This article aimed to present a realistic approach to the practical application of quantum mechanics in cybersecurity. It is no longer science fiction but a fact—facts that could be widely applied in the future. Anyone attempting to break or compromise such a system will need to understand technical aspects that go beyond basic computer science or mathematics and delve into quantum mechanics. Early familiarity with the topic may, or rather will, be crucial for the future of cybersecurity and cyber warfare.
the website I used to generate the diagrams: translator.globe.engineer
Specifically for: xss.is
Table of Contents:
Нажмите, чтобы раскрыть...
- Introduction to QKD
- Current state of quantum technologies
- Importance in critical infrastructure
- Implementation Sectors
- Quantum Fundamentals
- Understanding superposition
- Quantum entanglement explained
- Heisenberg's uncertainty principle
- No-cloning theorem and its implications
- Einstein's "spooky action at a distance"
- Development of quantum protocols
- Evolution of quantum cryptography
- Technical Specifications
- QBER definition and significance
- Key rate equations
- Practical implementation parameters
- QKD Protocols Overview
- Discrete/Continuous Variable protocols (DV-QKD) / (CV-QKD)
- Protocol comparison and applications
- Current Limitations
- Future Implications
- Impact on cybersecurity
- Integration with existing systems
Hello everyone! Today, I will focus on Quantum Key Distribution (QKD), as of all the technologies based on quantum mechanics, theory, and research, this one is the most empirically confirmed. It is also the most likely to be quickly implemented in the most sensitive infrastructures. In this first part 1/2 of the article, I will focus on general theory, basics, and potential implementations, and in part 2, I will specifically address potential vulnerabilities and attacks on this technology.
QKD is currently in various stages of implementation and testing in the following sectors:
Energy Sector:
Confirmed implementation at China State Grid
Pilot projects under EuroQCI
Security tests on SCADA systems in selected locations
Financial Sector:
Implementation in select banks in China (Bank of China, ICBC)
Pilot projects in other financial institutions
Security tests for high-value transactions
Military Infrastructure:
Research and development conducted by defense agencies
Demonstrations of the technology in satellite communications
Investments in quantum threat countermeasures
Telecommunications Sector:
Commercial deployments by China Telecom
Pilot projects with BT and Toshiba
Tests in backbone networks
So, let's begin!
QUANTUM KEY DISTRIBUTION (QKD):
(this fragment was quoted from this source: https://core.ac.uk/download/pdf/329118533.pdf)The act of safely exchanging a secret key between users over an insecure channel. Quantum key cryptography relies on quantum physics, specifically the quantum laws that complicate power consumption increases through quantum polarization. Fiber optic channels are used to transmit messages. In 1984, Quantum Key Distribution was first introduced, when Gilles Brassard and Charles Bennett developed the BB84 protocol. After the development of this protocol, many others followed. It is very difficult for attackers to eavesdrop on fiber optic channels. If a message is corrupted or attacked, the amount of corruption can be detected. This is used in BB84. Entangled objects shared between users form the basis of the Entanglement-Based (EB) protocol.
Нажмите, чтобы раскрыть...
Код: Скопировать в буфер обмена
|ψ⟩ = α|0⟩ + β|1⟩, where |α|² + |β|² = 1This quantum state represents the fundamental unit of quantum information (qubit).
To understand how this works, I must discuss the basic principles on which this distribution is based and why it is considered the highest known level of security in data transmission. Let's start with the most important concept—superposition: Imagine a coin. A normal coin has two sides: heads and tails. Before you toss it, you don’t know which side will be up, right? It could be heads or tails. You could also say it’s in an intermediate state, where it’s both heads and tails—until you check it. This is somewhat like superposition.
In the quantum world, instead of coins, we have particles, such as photons (particles of light). These particles can also be in multiple states "at once" until we measure them. For example, they can be in a superposition of polarization, vibrating both vertically and horizontally at the same time. Only when we "check" (measure) them do they "decide" on a specific state—vertical or horizontal.
QKD (Quantum Key Distribution) is a way to create a super-secret key to encrypt messages, thanks to superposition and another quantum trick called "entanglement". Entanglement: is like two magical coins that always land on the same side, no matter how far apart they are. Imagine you have one coin, and your friend has the other—on another continent! When you toss your coin and get heads, you instantly know that your friend’s coin is also heads, even though they haven’t tossed theirs yet. And the same goes if it were tails. It’s as if these coins are connected by an invisible thread and "talk" to each other instantly!
In the quantum world, entangled particles, like photons, behave similarly. If you measure the state of one entangled photon (for example, its polarization), you immediately know the state of the other entangled photon, even if it’s light-years away. You might think this sounds a bit "magical," but that’s how the quantum world works. And it’s this quantum entanglement, along with superposition, that makes QKD so secure. Any attempt to "eavesdrop" on these entangled photons by an outsider "breaks" them and changes their state, immediately revealing the presence of a spy. Speaking of measurement, let’s move on to Heisenberg’s Uncertainty Principle:
This principle, in short, tells us that in the quantum world, you can’t simultaneously know certain pairs of properties of particles, such as position and momentum (speed), with precision. The more accurately you know one, the less accurately you know the other. This isn’t due to imperfect instruments; it’s a fundamental property of the universe and a limitation of nature! Imagine it like this: you’re trying to take a photo of a small, fast hamster. You want to know where it is and how fast it’s running. The problem is, if you use a fast shutter speed to see exactly where it is, the hamster will be blurry, and you won’t know how fast it’s running. And if you use a long exposure to see how fast it’s running, the hamster will have moved, and you won’t know exactly where it was when you took the picture.
The last fundamental concept is the No-Cloning Theorem: Imagine you have a magic playing card that changes color every time you look at it—sometimes it’s red, sometimes blue, sometimes green. And you want to make a perfect copy of it. The problem is, every time you try to "read" it to copy it, its color changes! You’ll never be sure what color it originally was, so you’ll never make a perfect copy.
The no-cloning theorem in quantum mechanics states that you can’t make a perfect copy of an unknown quantum state, just like you can’t copy the color of this magic card. This is key to QKD security: if someone tries to "eavesdrop" on a quantum message (i.e., make a copy), they irreversibly change its original state, which the sender and receiver will immediately detect. It’s as if someone destroyed your magic card by trying to copy it.
As you now understand, thanks to superposition and entanglement, QKD allows the creation of a key that only the sender and receiver know is secure, and thanks to the No-Cloning Theorem, anyone who tries to intercept it will be instantly detected.
One last thing I’d like to mention on this topic is a brief history. Remember the "magic coins" I mentioned? Einstein had something very interesting to say about this phenomenon (quantum entanglement)—he called it "spooky action at a distance." Why spooky? Because even one of the greatest physicists in history was deeply troubled by this phenomenon! Einstein couldn’t grasp how it was possible that when you toss your coin, you instantly know that your friend’s coin also landed the same way, even though they hadn’t tossed theirs yet, and they’re thousands of kilometers away!
According to Einstein’s theory of relativity, nothing can travel faster than light—it’s the cosmic speed limit. And yet these entangled particles seem to "know" about each other instantly, no matter the distance between them. It’s as if they’re connected by some invisible, instantaneous bond that breaks the rules of relativity!
But here’s a small catch (there’s always one, right?). Even though these particles behave in such a strange way, we can’t use them to send messages faster than light. It’s a bit like twins who always dress oppositely—if one wears a black shirt, the other will definitely wear white. But until they meet and compare outfits (in our case, compare measurement results), we don’t know which twin is wearing which color!
Einstein remained skeptical of quantum mechanics for the rest of his life, precisely because of these "spooky" behaviors. He believed there must be some "hidden variables"—something we hadn’t discovered yet—that would explain these strange phenomena in a more "normal" way. However, experiments conducted many years later (especially those related to Bell’s inequalities) showed that Einstein was wrong—the quantum world really is as strange as it seems!
According to Einstein’s theory of relativity, nothing can travel faster than light—it’s the cosmic speed limit. And yet these entangled particles seem to "know" about each other instantly, no matter the distance between them. It’s as if they’re connected by some invisible, instantaneous bond that breaks the rules of relativity!
But here’s a small catch (there’s always one, right?). Even though these particles behave in such a strange way, we can’t use them to send messages faster than light. It’s a bit like twins who always dress oppositely—if one wears a black shirt, the other will definitely wear white. But until they meet and compare outfits (in our case, compare measurement results), we don’t know which twin is wearing which color!
Einstein remained skeptical of quantum mechanics for the rest of his life, precisely because of these "spooky" behaviors. He believed there must be some "hidden variables"—something we hadn’t discovered yet—that would explain these strange phenomena in a more "normal" way. However, experiments conducted many years later (especially those related to Bell’s inequalities) showed that Einstein was wrong—the quantum world really is as strange as it seems!
QBER (Quantum Bit Error Rate) is a key parameter determining the quality of quantum transmission:
Код: Скопировать в буфер обмена
Код:
QBER = (number of erroneous bits) / (total number of received bits)
Typically, an acceptable QBER for secure transmission is < 11%.The equation for determining the theoretical key generation rate (Key Rate) in the BB84 protocol is:
Код: Скопировать в буфер обмена
R = q(-Qμ f(Eμ)H2(Eμ) + Q1[1-H2(e1)])where:
- q is the protocol efficiency factor (for BB84 q = 1/2)
- Qμ is the gain coefficient
- Eμ is QBER
- f(x) is the error correction efficiency
- H2(x) is Shannon’s binary entropy
- Q1 is the probability of detecting a single photon
- e1 is QBER for single photons
DV-QKD:
BB84 (Most common): The pioneering protocol, using the polarization of single photons. The sender (Alice) sends photons encoded in randomly chosen bases (e.g., vertical/horizontal or diagonal), and the receiver (Bob) randomly chooses measurement bases. After transmission, Alice and Bob publicly compare chosen bases, discarding results from incompatible bases. The remaining results form the raw key. Security is based on the uncertainty principle (mentioned earlier) and the No-Cloning Theorem—an eavesdropper (Eve) attempting to intercept and copy the photons will introduce detectable errors.
E91 (Ekert91):
Uses entangled pairs of photons. Alice and Bob each receive one photon from the entangled pair and perform measurements in different bases. Security arises from the violation of Bell's inequality in the event of eavesdropping. Eavesdropping is detected through statistical analysis of the correlations between Alice's and Bob's measurements.
SARG04:
A modification of BB84, it uses only one basis for encoding information and the other as "bait" for the eavesdropper. This increases efficiency compared to BB84 but is slightly less resistant to noise.
CV-QKD:
GG02 (Grosshans & Grangier 02):
Utilizes quadrature components of coherent light (lasers). The key is encoded in the amplitudes and phases of light pulses, measured by Bob. Security is based on the uncertainty principle for continuous variables. This protocol is relatively easy to implement using standard telecommunications technology.
There are also hybrid protocols and other variants, but the ones listed are the most significant and representative of different approaches to QKD.
Practical Implementation Details:
Existing QKD Networks:
- Tokyo QKD Network: Operational since 2010, connecting multiple research institutions
- China's Beijing-Shanghai Backbone: World's longest QKD network (2,000+ km)
- European QKD Networks: Several test networks in operation (SwissQuantum, SECOQC)
Quantum Memory in QKD
Quantum memory is crucial for extending QKD networks:
- Allows storage of quantum states for repeater operations
- Current limitations: Short coherence times (microseconds to milliseconds)
- Research focus: Room-temperature quantum memories using diamond NV centers
of course QKD is not perfect on every level and like any new technology, it requires solving currently known problems, the most problematic of which are:
Range Limitations, current practical limitations:
- Direct fiber links: ~100 km without quantum repeaters
- Satellite QKD: Limited by atmospheric conditions and satellite visibility
Implementation Challenges:
- Detector technology limitations
- Environmental interference
- Need for dedicated fiber lines
- Cost of single-photon sources
Conclusions:
QKD has enormous potential in ensuring the security of information transmission. Although there are technological and economic challenges, intensive research and development are driving progress in terms of range, cost, and integration. QKD is a technology worth attention and further development. This article aimed to present a realistic approach to the practical application of quantum mechanics in cybersecurity. It is no longer science fiction but a fact—facts that could be widely applied in the future. Anyone attempting to break or compromise such a system will need to understand technical aspects that go beyond basic computer science or mathematics and delve into quantum mechanics. Early familiarity with the topic may, or rather will, be crucial for the future of cybersecurity and cyber warfare.
the website I used to generate the diagrams: translator.globe.engineer