D2
Администратор
- Регистрация
- 19 Фев 2025
- Сообщения
- 4,380
- Реакции
- 0
Author: ski
specially for xss.is
part: 1
Hello XSS fam <3, this is my first article. I hope everyone will love it <3
in this article i shared basic of DFIR into Mobile phones, in future we will go more deeper :smile10:
:smile10:
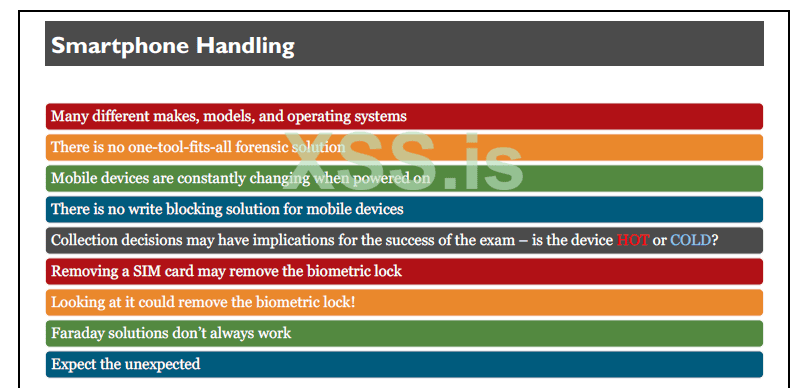
Mobile devices, including smartphones, present a variety of unique challenges to investigators involved in forensic examinations of data from these devices. Part of the challenge arises from the fact that there are so many different makes and models of phones using a variety of underlying operating systems. Because of this, there is no one-size-fits-all forensic solution for mobile devices, and in many cases, numerous tools may need to be used to obtain the data needed for a particular investigation.
Additionally, traditional digital forensics concepts may not apply due to the way flash memory functions. Mobile devices are constantly changing when powered on, and there is no way to write block a mobile device because they communicate using modem protocols, such as AT commands and others. Because of these factors the goal in forensics is to make as little change as possible and to document those changes that were made to the device during the forensic process Just powering on a smartphone generates changes to the data and traces that can be observed of the device. This is true even if the user does not operate the device other than just powering it on.
The device, once powered on, reaches out to the mobile network to authenticate on the system and may store last location data related to mobile towers or GPS if it is enabled.
At some point, however, with few exceptions, the phone most likely must be turned on in order to work with it, unless the capability for data extraction through physical, JTAG, ISP (In System Programming), or chip-off methods exists.
A HOT device would be one that was recently unlocked with the passcode by the user. A COLD device would be one that was freshly restarted and has yet to be unlocked. These concepts make a difference in handling and how the tool can access the data.

Method 1: Always Off Rule for Cell Phones
This method works well if there will be a time delay in examination of the phone that could potentially result in battery discharge and data loss:
• Seize the phone and turn it off
• May remove the battery to prevent phone from accidentally being turned on
• Only turn the phone on when a trusted tool directs you to do so
The benefits of turning off the phone during collection include:
• Preserving call logs and last cell tower location information (LOCI)
• Preventing overwriting deleted data
• Preventing data destruction signals from reaching the mobile phone
• Preventing improper mobile phone handling (for example placing calls, sending messages, taking photos, or deleting files)
The risks of turning off the mobile phone include possibly engaging protection mechanisms, such as encryption, passwords, PIN codes, and more. Turning off the phone also results in loss of data from RAM. Make sure to use caution when turning off a device that was HOT (aka. Recently unlocked with a passcode) as this may be your only chance to get the most thorough dump of data from that phone.
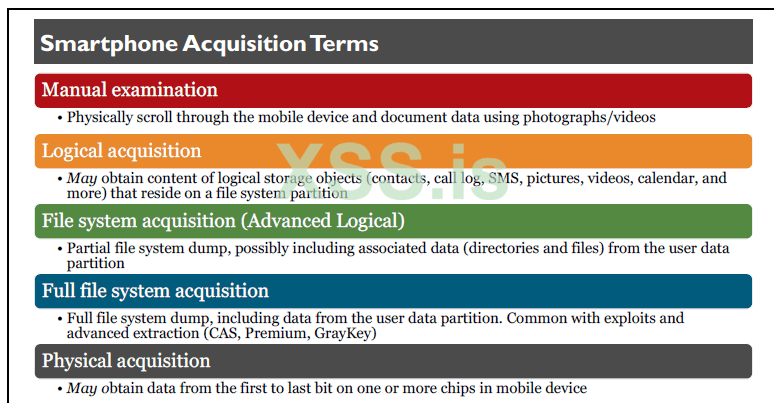
There are five basic levels of acquisition for smartphones, including:
•Manual examination: Process undertaken when the examiner physically scrolls through the mobile device and documents data using photographs or written notes regarding the contents of the device.
•Logical acquisition: Obtaining specific contents of logical storage objects that reside on a file system partition within a mobile device. A tool that communicates with the phone and obtains and reports only existing non-deleted contacts, call history records, SMS text messages, pictures, videos, or one or more items from the previously listed categories is conducting a logical acquisition of the data from the device.
•File system acquisition/Advanced Logical: Partial file system dump. Physical analyzer uses the term “Advanced Logical” for some smart devices, more commonly iOS devices. If we think about “iOS Advanced Logical” it is a partial file system obtained through backup + AFC, if we think about “Android Advanced Logical” it is again a partial file system obtained through backup + MTP + ADB.
•Full file system: Full file system dump, including data from the user data partition. Common with exploits and advanced extraction (CAS, Premium, GrayKey). This is the next best thing to a full physical acquisition.
•Physical acquisition: Use of the term physical acquisition in mobile-device forensics refers to the process of obtaining all the data from first to last bit from one or more physical stores (memory chips) in the mobile device. JTAG, ISP, and chip-off methods fall under physical acquisition. The ability to obtain this type of extraction is becoming rare as encryption mechanisms are constantly growing in strength.
When performing smartphone forensics, it is ideal to first obtain the deepest level of acquisition supported for the make and model of phone you’re working on that the tools you are using will support. Then go back and complete other supported extraction methods that may do a better job of parsing and displaying data from the phone.
For example, if you are able to obtain a physical memory dump from the phone, you get deleted information and files that are locked by the OS when they are in use. You may also be able to obtain security and unlock codes with a physical acquisition. The tool you are using, however, may or may not parse user data in an easily readable format with a physical acquisition.
Therefore, if you next perform a file system and/or logical acquisition of the data, you may obtain better results. Finally, taking pictures of particularly important pieces of data from the device.

It is important not only to know how to use the mobile forensic tools you have access to, but also to know what they are doing when you process a phone. Different mobile forensic tools use different methods to access and acquire the data from different makes and models of phones. The tool itself often makes changes to the data on the phone, including the installation of bootloaders or applications, or use of jailbreaking and rooting methods. These methods are acceptable and necessary to obtain data from the devices, but it is advisable to know what your tools are doing for each phone. It’s important for you to understand how these exploits work and how the tools leverage them. Another reason to know what your tools are doing is that you may find different methods to use the tool to obtain better results.
For example, with Cellebrite Physical Analyzer, on many Android-based devices, using Generic Android Methods under the File System acquisition option may parse more data into usable format than a successfully supported physical acquisition of the same model of phone.
Sometimes, tools may make changes to the original device during acquisition that affect subsequent acquisition attempts. For example, when performing acquisitions on newer iPhones, Oxygen applies an encryption password to devices that have not had a previously encrypted backup, without notification to the examiner. If the examiner attempts a subsequent acquisition using Cellebrite or another tool, they will be asked to supply the encryption password applied by Oxygen during the parsing process, though that password is not well documented. The password is “oxygen”. Cellebrite uses “1234” or “12345” and Magnet uses “mag123” when backup encryption is applied to the extraction. This information isn’t readily available in the documentation, and Elcomsoft Phone Breaker was used to solve the puzzle of what the password was. keep in mind this may happen to you and you may find yourself having to crack a password you and the user did not set on the device.

For older Android devices, we can perform full physical extractions of data using a small program or set of instructions called a “bootloader”. The bootloader is injected into the RAM of the device and executes before the operating system boots. Bootloaders are usually a generic solution, based upon a family of devices, often defined by the chipset in the phone. They are designed to be read-only and are therefore considered safe and forensically sound.
Bootloaders allow for complete acquisition of flash memory of a mobile device, including spare area of the flash memory. Manufacturers of cell phone forensic tools will often create custom bootloaders for full physical acquisition purposes. In order to use a bootloader for acquisition, sometimes the phone must be put into rescue or recovery mode, or a specialized cable might be necessary. Sometimes firmware update protocols are used to insert a bootloader.
When a device is locked, it may be possible to use Android’s recovery partition to access the data on the device. The Android device needs to be placed into recovery mode so the custom recovery image can be pushed to the device. A custom recovery is a third-party image that replaces the stock Android recovery partition and allows the user to gain access to the data or root the device. Again, this is only supported for older, non-encrypted Android devices. A common custom recovery partition is Team Win Recovery Project(TWRP).
EDL mode is available with some Qualcomm chips and can allow low-level access to the chipset. This is designed to allow for device analysis, repair, or re-flashing, but can present the opportunity to achieve a full physical extraction of the data from the chip. EDL mode can be accessed by several software methods, including:
• Special key combinations: Depending on the manufacturer, the key combination may be different. The most common combination from a powered-off state is: Hold Vol Up + Vol Down while connecting USB. Other combinations may include Vol Up, Vol Up + Vol Down + Power, etc. Some vendors have early boot menus that offer the choice of entering the mode (recovery, fastboot, download).
• ADB: Most phones with EDL available allow entry to EDL mode via a command available from an authorized ADB session. (Try: adb reboot edl.) This is useful for obtaining a physical extraction of an unlocked device. This is what Cellebrite UFED attempts when trying "Generic Qualcomm ADB".
• Fastboot: An alternative vendor-specific method exists from the fastboot mode, which is sometimes reachable by other key combinations (usually Vol Down + Power).
• FTM: Some vendors have implemented FTM mode (hold Vol Down while connecting the USB), which exposes an ADB interface. Cellebrite UFED can detect this mode and continue to extract normally using the "Generic Qualcomm ADB" method.
Hardware methods may include:
• EDL cable: Some devices will detect a special cable that will signal the device to enter EDL. Specialized cables may be obtained from various stores and will be supplied by Cellebrite to customers when the phone is supported.
• Test points: Some devices have test points that, when shorted to ground, will cause the device to enter into EDL mode. Depending on the board, they may be easily accessible, even without significant disassembly.
Cellebrite offers additional methods to acquire Android devices that are newer and otherwise inaccessible. These include Qualcomm Live, MTK Live and the latest capability referred to as Huawei (Kirin Live). These extraction methods are linked to the chip inside of the Android and are accessible via UFED.
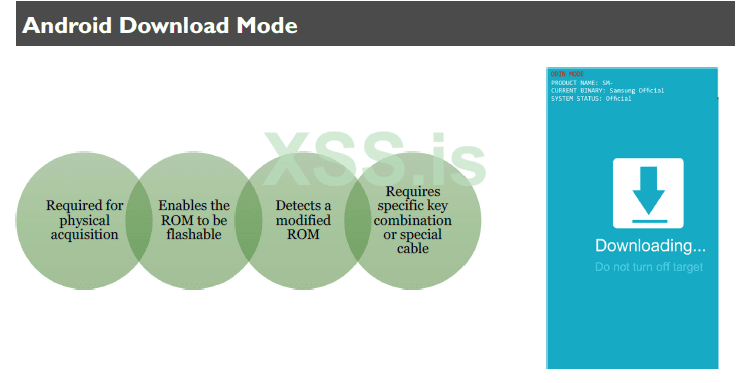
Most commercial tools that attempt to physically acquire an Android device require that the device enter a mode referred to as Download Mode. Download Mode allows the user to flash the ROM of the device, which then allows the tool to create a forensic image. Flashing the ROM leaves traces on the device. When the custom ROM of the device is modified, it’s tracked within the device. When the device enters Download Mode, the number of flash counts (ROM changes) are listed To enter Download Mode, a specific cable or key combination may be required. Each device may have a unique key combination required. The easiest way to get into Download Mode is to follow the instructions provided by the forensic tool.

The screenshot shows a device that has the original, custom ROM and has not been modified by a forensic tool or user. If a device ROM had been modified, the CUSTOM BINARY DOWNLOAD indicator would say YES or retain the count for the number of times it was flashed, and the CURRENT BINARY may reference something like CUSTOM (or anything other than the OFFICIAL binary that shipped with the device). Keep in mind, your forensic tools make these modifications.
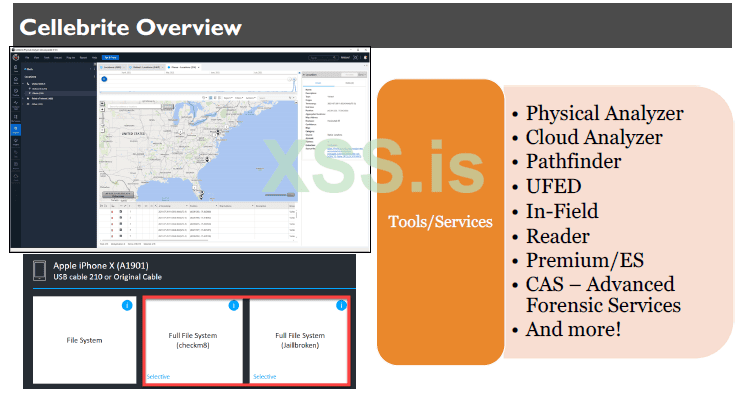
Cellebrite's mobile forensic solutions include a combination of hardware, software, and services designed for extracting and analyzing data from mobile devices. These tools are some of the most popular in mobile device forensics. Cellebrite is strong at application parsing, timelining and carving additional artifacts. Physical Analyzer is a great platform for conducting analysis as it provides support for almost all mobile platforms and shows you both the phone extraction image file and the file system for examiners to dig into data that isn’t parsed.
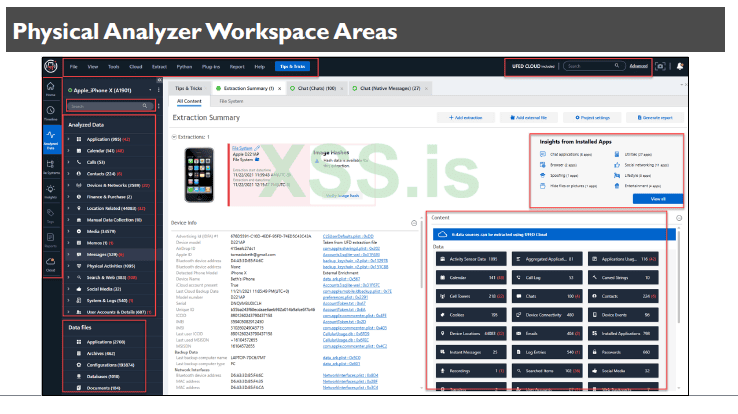
For those new to this tool, the more you use it, the easier it becomes. The key areas highlighted are the toolbar, where many features are accessible.
A logical keyword search or an Advanced Search at the top right, which lets you search generically for a keyword or as an “and” or “or” request. This also includes the ability to conduct an “in content” search which takes some time but will dive into files that are not parsed by the tool.
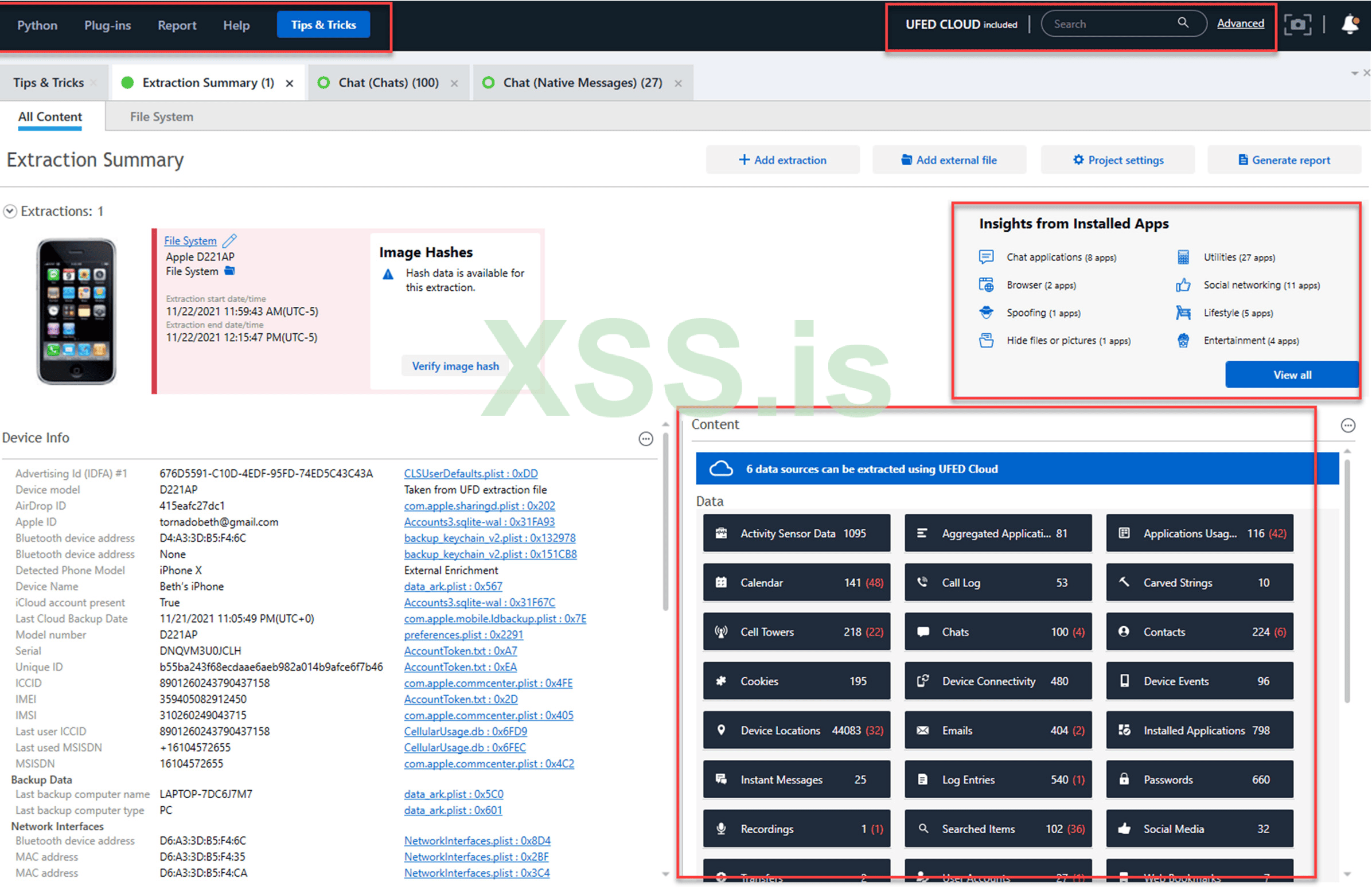
to be continued….
specially for xss.is
part: 1
Hello XSS fam <3, this is my first article. I hope everyone will love it <3
in this article i shared basic of DFIR into Mobile phones, in future we will go more deeper
Mobile devices, including smartphones, present a variety of unique challenges to investigators involved in forensic examinations of data from these devices. Part of the challenge arises from the fact that there are so many different makes and models of phones using a variety of underlying operating systems. Because of this, there is no one-size-fits-all forensic solution for mobile devices, and in many cases, numerous tools may need to be used to obtain the data needed for a particular investigation.
Additionally, traditional digital forensics concepts may not apply due to the way flash memory functions. Mobile devices are constantly changing when powered on, and there is no way to write block a mobile device because they communicate using modem protocols, such as AT commands and others. Because of these factors the goal in forensics is to make as little change as possible and to document those changes that were made to the device during the forensic process Just powering on a smartphone generates changes to the data and traces that can be observed of the device. This is true even if the user does not operate the device other than just powering it on.
The device, once powered on, reaches out to the mobile network to authenticate on the system and may store last location data related to mobile towers or GPS if it is enabled.
At some point, however, with few exceptions, the phone most likely must be turned on in order to work with it, unless the capability for data extraction through physical, JTAG, ISP (In System Programming), or chip-off methods exists.
A HOT device would be one that was recently unlocked with the passcode by the user. A COLD device would be one that was freshly restarted and has yet to be unlocked. These concepts make a difference in handling and how the tool can access the data.
Method 1: Always Off Rule for Cell Phones
This method works well if there will be a time delay in examination of the phone that could potentially result in battery discharge and data loss:
• Seize the phone and turn it off
• May remove the battery to prevent phone from accidentally being turned on
• Only turn the phone on when a trusted tool directs you to do so
The benefits of turning off the phone during collection include:
• Preserving call logs and last cell tower location information (LOCI)
• Preventing overwriting deleted data
• Preventing data destruction signals from reaching the mobile phone
• Preventing improper mobile phone handling (for example placing calls, sending messages, taking photos, or deleting files)
The risks of turning off the mobile phone include possibly engaging protection mechanisms, such as encryption, passwords, PIN codes, and more. Turning off the phone also results in loss of data from RAM. Make sure to use caution when turning off a device that was HOT (aka. Recently unlocked with a passcode) as this may be your only chance to get the most thorough dump of data from that phone.
There are five basic levels of acquisition for smartphones, including:
•Manual examination: Process undertaken when the examiner physically scrolls through the mobile device and documents data using photographs or written notes regarding the contents of the device.
•Logical acquisition: Obtaining specific contents of logical storage objects that reside on a file system partition within a mobile device. A tool that communicates with the phone and obtains and reports only existing non-deleted contacts, call history records, SMS text messages, pictures, videos, or one or more items from the previously listed categories is conducting a logical acquisition of the data from the device.
•File system acquisition/Advanced Logical: Partial file system dump. Physical analyzer uses the term “Advanced Logical” for some smart devices, more commonly iOS devices. If we think about “iOS Advanced Logical” it is a partial file system obtained through backup + AFC, if we think about “Android Advanced Logical” it is again a partial file system obtained through backup + MTP + ADB.
•Full file system: Full file system dump, including data from the user data partition. Common with exploits and advanced extraction (CAS, Premium, GrayKey). This is the next best thing to a full physical acquisition.
•Physical acquisition: Use of the term physical acquisition in mobile-device forensics refers to the process of obtaining all the data from first to last bit from one or more physical stores (memory chips) in the mobile device. JTAG, ISP, and chip-off methods fall under physical acquisition. The ability to obtain this type of extraction is becoming rare as encryption mechanisms are constantly growing in strength.
When performing smartphone forensics, it is ideal to first obtain the deepest level of acquisition supported for the make and model of phone you’re working on that the tools you are using will support. Then go back and complete other supported extraction methods that may do a better job of parsing and displaying data from the phone.
For example, if you are able to obtain a physical memory dump from the phone, you get deleted information and files that are locked by the OS when they are in use. You may also be able to obtain security and unlock codes with a physical acquisition. The tool you are using, however, may or may not parse user data in an easily readable format with a physical acquisition.
Therefore, if you next perform a file system and/or logical acquisition of the data, you may obtain better results. Finally, taking pictures of particularly important pieces of data from the device.
It is important not only to know how to use the mobile forensic tools you have access to, but also to know what they are doing when you process a phone. Different mobile forensic tools use different methods to access and acquire the data from different makes and models of phones. The tool itself often makes changes to the data on the phone, including the installation of bootloaders or applications, or use of jailbreaking and rooting methods. These methods are acceptable and necessary to obtain data from the devices, but it is advisable to know what your tools are doing for each phone. It’s important for you to understand how these exploits work and how the tools leverage them. Another reason to know what your tools are doing is that you may find different methods to use the tool to obtain better results.
For example, with Cellebrite Physical Analyzer, on many Android-based devices, using Generic Android Methods under the File System acquisition option may parse more data into usable format than a successfully supported physical acquisition of the same model of phone.
Sometimes, tools may make changes to the original device during acquisition that affect subsequent acquisition attempts. For example, when performing acquisitions on newer iPhones, Oxygen applies an encryption password to devices that have not had a previously encrypted backup, without notification to the examiner. If the examiner attempts a subsequent acquisition using Cellebrite or another tool, they will be asked to supply the encryption password applied by Oxygen during the parsing process, though that password is not well documented. The password is “oxygen”. Cellebrite uses “1234” or “12345” and Magnet uses “mag123” when backup encryption is applied to the extraction. This information isn’t readily available in the documentation, and Elcomsoft Phone Breaker was used to solve the puzzle of what the password was. keep in mind this may happen to you and you may find yourself having to crack a password you and the user did not set on the device.
For older Android devices, we can perform full physical extractions of data using a small program or set of instructions called a “bootloader”. The bootloader is injected into the RAM of the device and executes before the operating system boots. Bootloaders are usually a generic solution, based upon a family of devices, often defined by the chipset in the phone. They are designed to be read-only and are therefore considered safe and forensically sound.
Bootloaders allow for complete acquisition of flash memory of a mobile device, including spare area of the flash memory. Manufacturers of cell phone forensic tools will often create custom bootloaders for full physical acquisition purposes. In order to use a bootloader for acquisition, sometimes the phone must be put into rescue or recovery mode, or a specialized cable might be necessary. Sometimes firmware update protocols are used to insert a bootloader.
When a device is locked, it may be possible to use Android’s recovery partition to access the data on the device. The Android device needs to be placed into recovery mode so the custom recovery image can be pushed to the device. A custom recovery is a third-party image that replaces the stock Android recovery partition and allows the user to gain access to the data or root the device. Again, this is only supported for older, non-encrypted Android devices. A common custom recovery partition is Team Win Recovery Project(TWRP).
EDL mode is available with some Qualcomm chips and can allow low-level access to the chipset. This is designed to allow for device analysis, repair, or re-flashing, but can present the opportunity to achieve a full physical extraction of the data from the chip. EDL mode can be accessed by several software methods, including:
• Special key combinations: Depending on the manufacturer, the key combination may be different. The most common combination from a powered-off state is: Hold Vol Up + Vol Down while connecting USB. Other combinations may include Vol Up, Vol Up + Vol Down + Power, etc. Some vendors have early boot menus that offer the choice of entering the mode (recovery, fastboot, download).
• ADB: Most phones with EDL available allow entry to EDL mode via a command available from an authorized ADB session. (Try: adb reboot edl.) This is useful for obtaining a physical extraction of an unlocked device. This is what Cellebrite UFED attempts when trying "Generic Qualcomm ADB".
• Fastboot: An alternative vendor-specific method exists from the fastboot mode, which is sometimes reachable by other key combinations (usually Vol Down + Power).
• FTM: Some vendors have implemented FTM mode (hold Vol Down while connecting the USB), which exposes an ADB interface. Cellebrite UFED can detect this mode and continue to extract normally using the "Generic Qualcomm ADB" method.
Hardware methods may include:
• EDL cable: Some devices will detect a special cable that will signal the device to enter EDL. Specialized cables may be obtained from various stores and will be supplied by Cellebrite to customers when the phone is supported.
• Test points: Some devices have test points that, when shorted to ground, will cause the device to enter into EDL mode. Depending on the board, they may be easily accessible, even without significant disassembly.
Cellebrite offers additional methods to acquire Android devices that are newer and otherwise inaccessible. These include Qualcomm Live, MTK Live and the latest capability referred to as Huawei (Kirin Live). These extraction methods are linked to the chip inside of the Android and are accessible via UFED.
Most commercial tools that attempt to physically acquire an Android device require that the device enter a mode referred to as Download Mode. Download Mode allows the user to flash the ROM of the device, which then allows the tool to create a forensic image. Flashing the ROM leaves traces on the device. When the custom ROM of the device is modified, it’s tracked within the device. When the device enters Download Mode, the number of flash counts (ROM changes) are listed To enter Download Mode, a specific cable or key combination may be required. Each device may have a unique key combination required. The easiest way to get into Download Mode is to follow the instructions provided by the forensic tool.
The screenshot shows a device that has the original, custom ROM and has not been modified by a forensic tool or user. If a device ROM had been modified, the CUSTOM BINARY DOWNLOAD indicator would say YES or retain the count for the number of times it was flashed, and the CURRENT BINARY may reference something like CUSTOM (or anything other than the OFFICIAL binary that shipped with the device). Keep in mind, your forensic tools make these modifications.
Cellebrite's mobile forensic solutions include a combination of hardware, software, and services designed for extracting and analyzing data from mobile devices. These tools are some of the most popular in mobile device forensics. Cellebrite is strong at application parsing, timelining and carving additional artifacts. Physical Analyzer is a great platform for conducting analysis as it provides support for almost all mobile platforms and shows you both the phone extraction image file and the file system for examiners to dig into data that isn’t parsed.
For those new to this tool, the more you use it, the easier it becomes. The key areas highlighted are the toolbar, where many features are accessible.
A logical keyword search or an Advanced Search at the top right, which lets you search generically for a keyword or as an “and” or “or” request. This also includes the ability to conduct an “in content” search which takes some time but will dive into files that are not parsed by the tool.
to be continued….